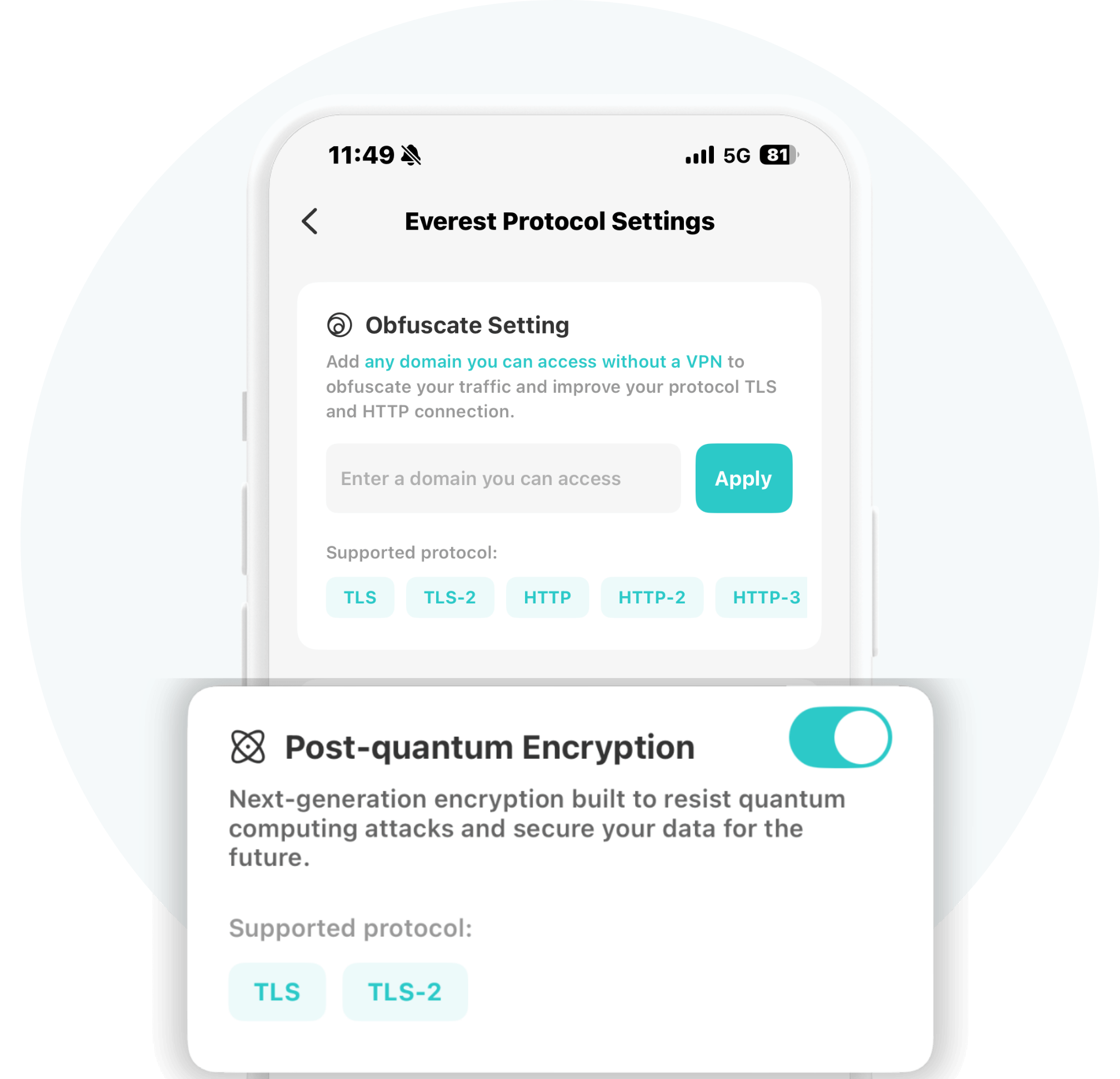
Step 1. Send Request
Before establishing a connection, a request will be sent to clarify the best server.
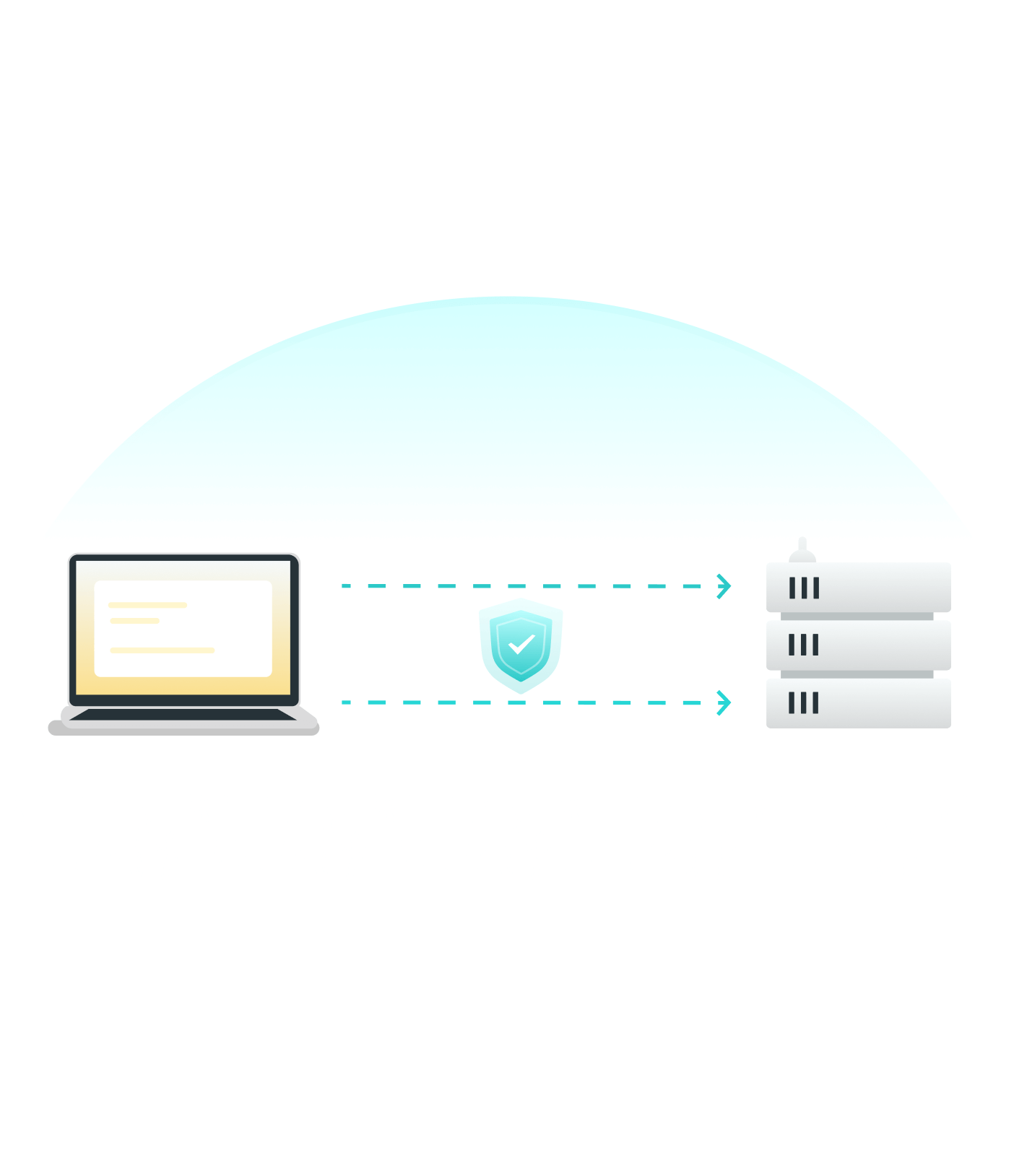
Step 2. Build a Secure Tunnel
Request received, a secure VPN tunnel will then be built between your device and the VPN server.
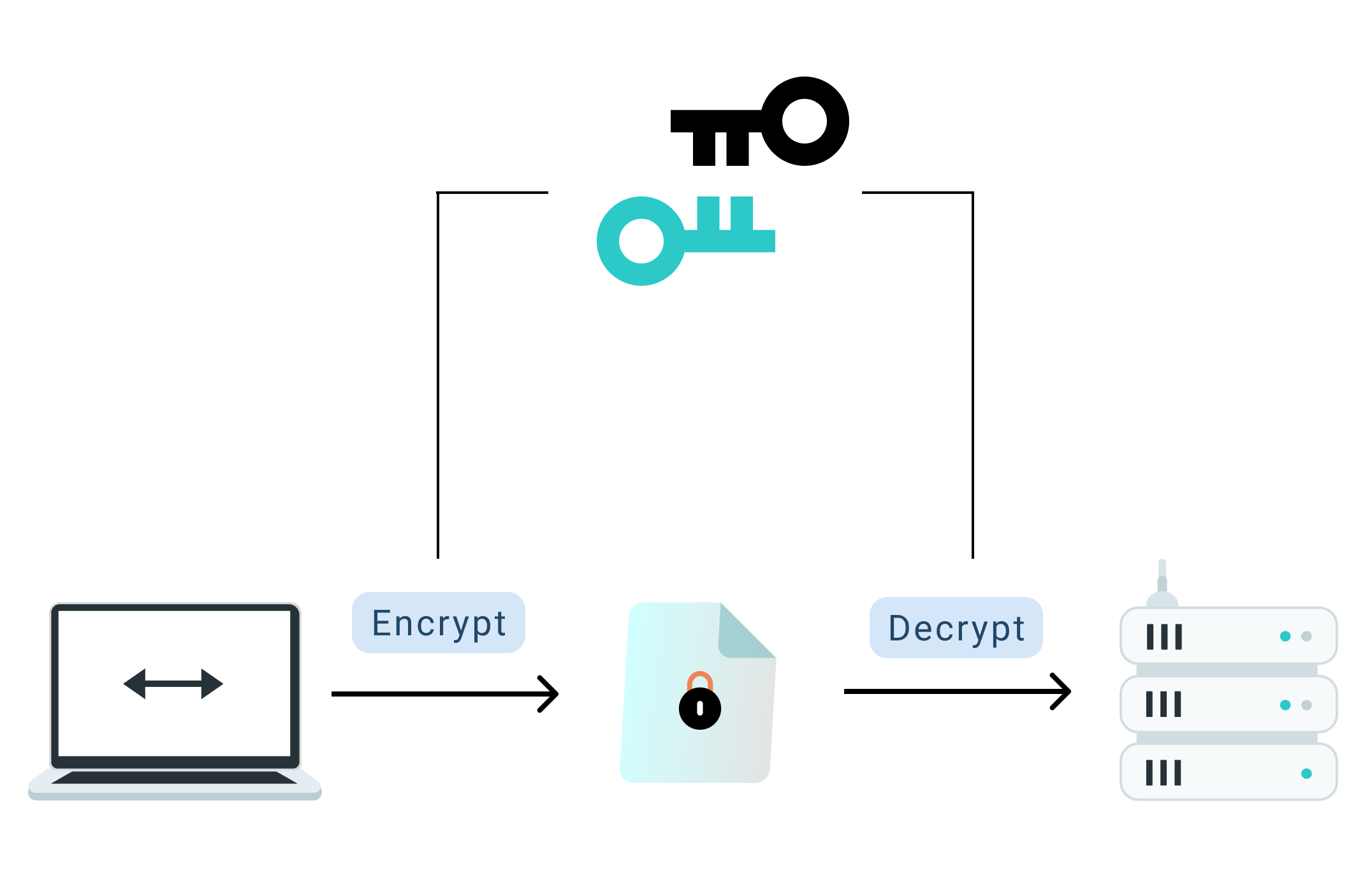
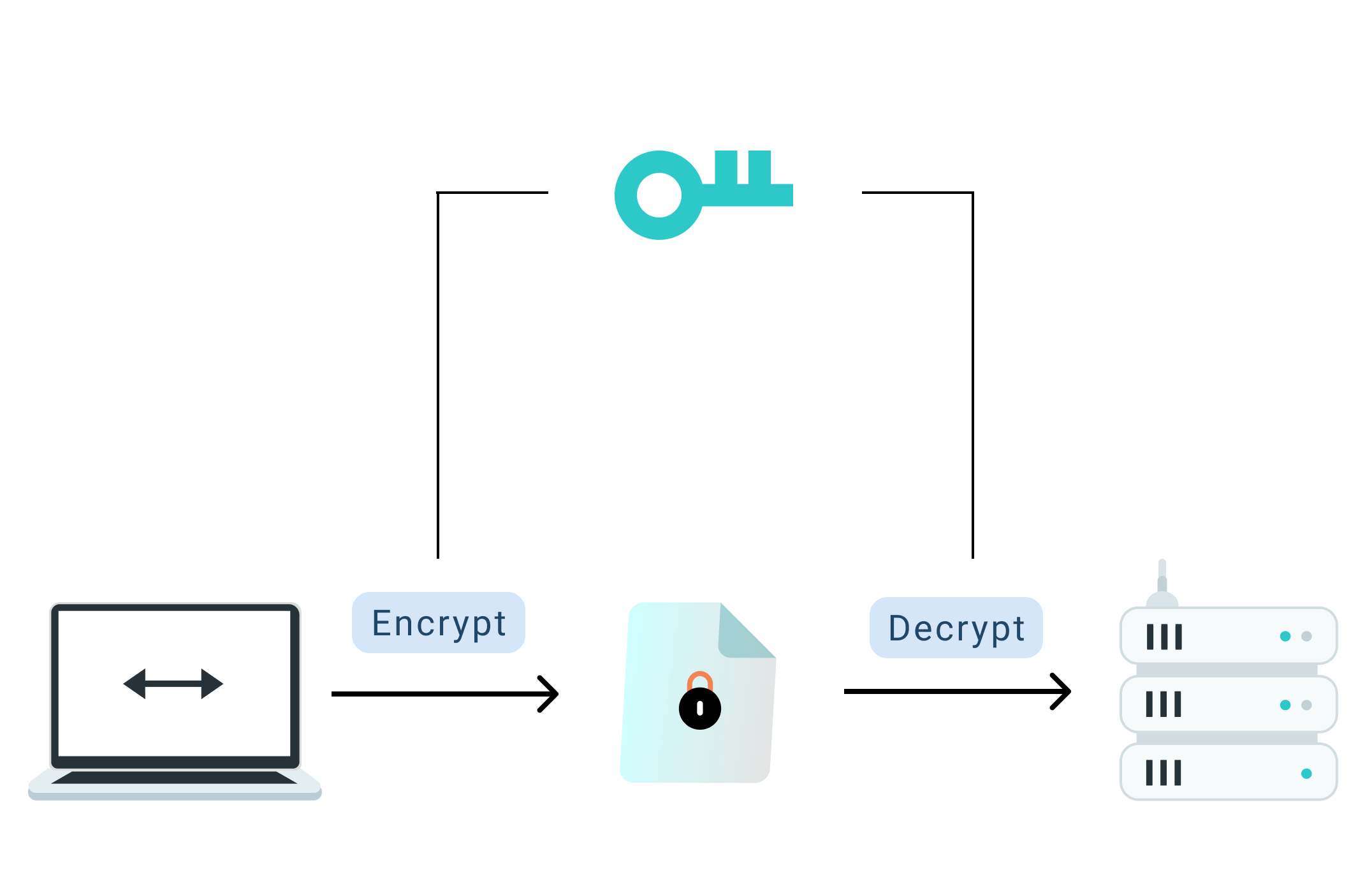
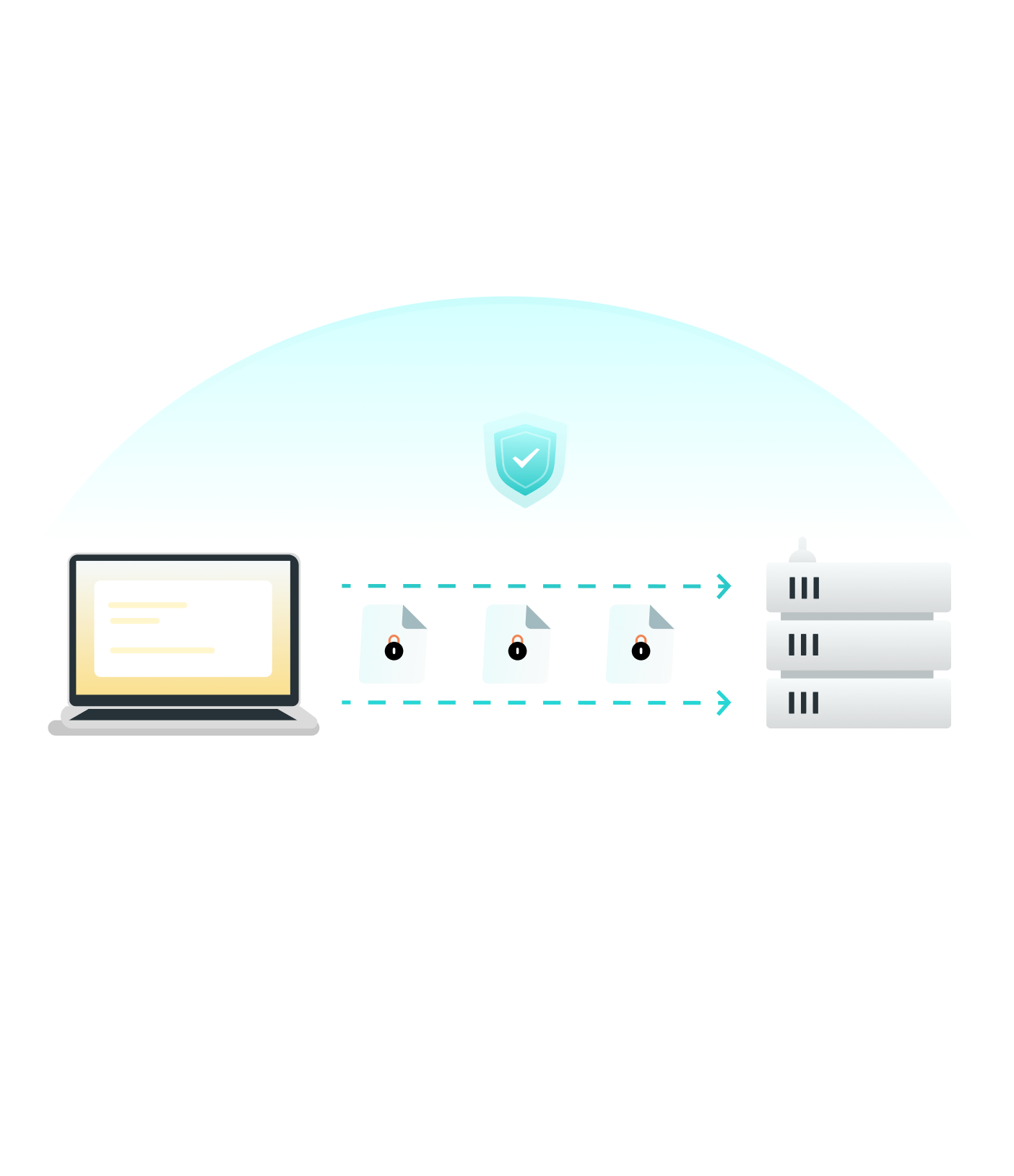
Step 3. Encrypt Data
Symmetric encryption is used for a secure “handshake” to verify identity and exchange a session key. Then, the connection seamlessly switches to fast symmetric encryption for all subsequent data.
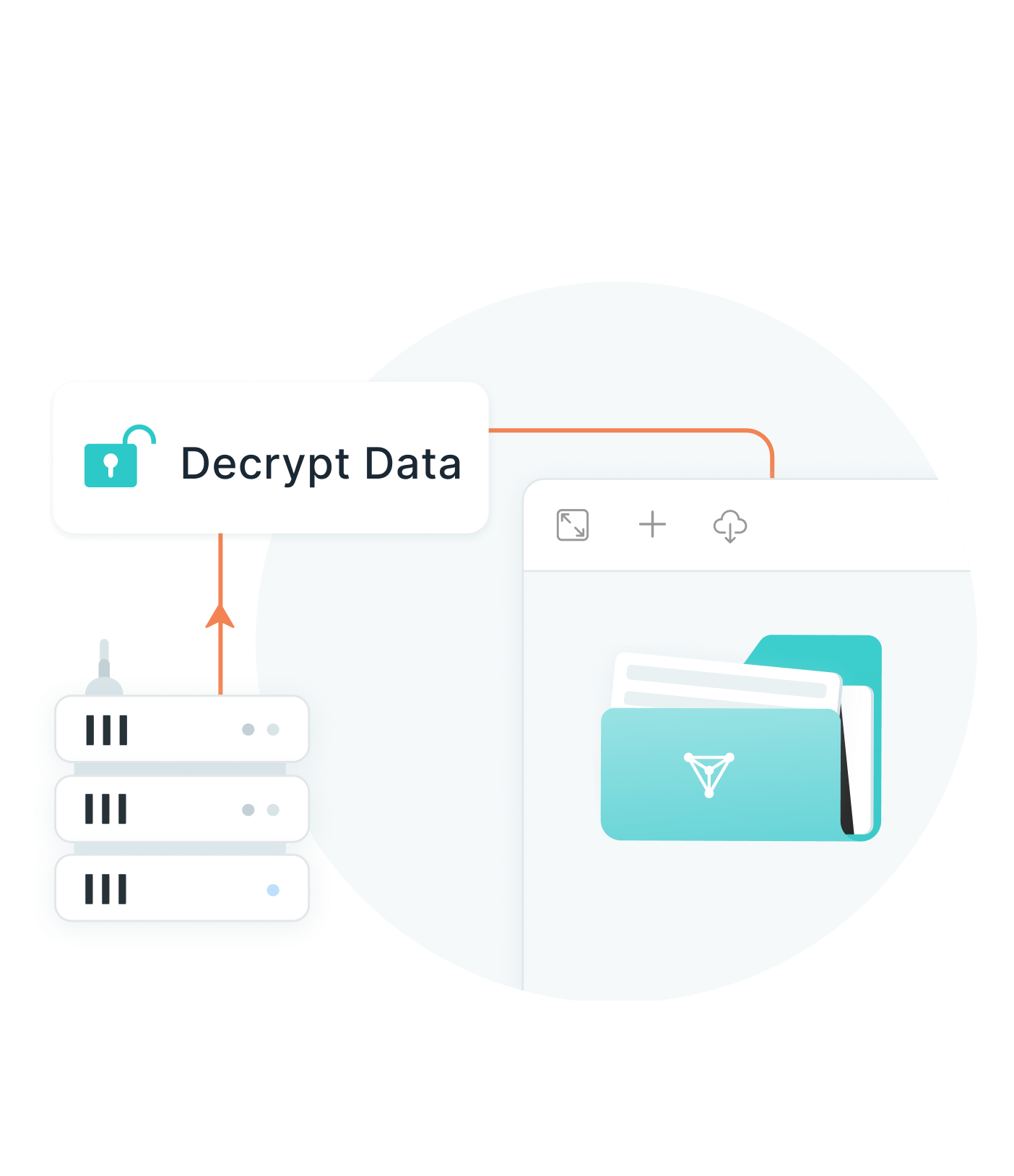
Step 4. Decrypt Data
The VPN server decrypts the data to its original text and sends it to the intended website.
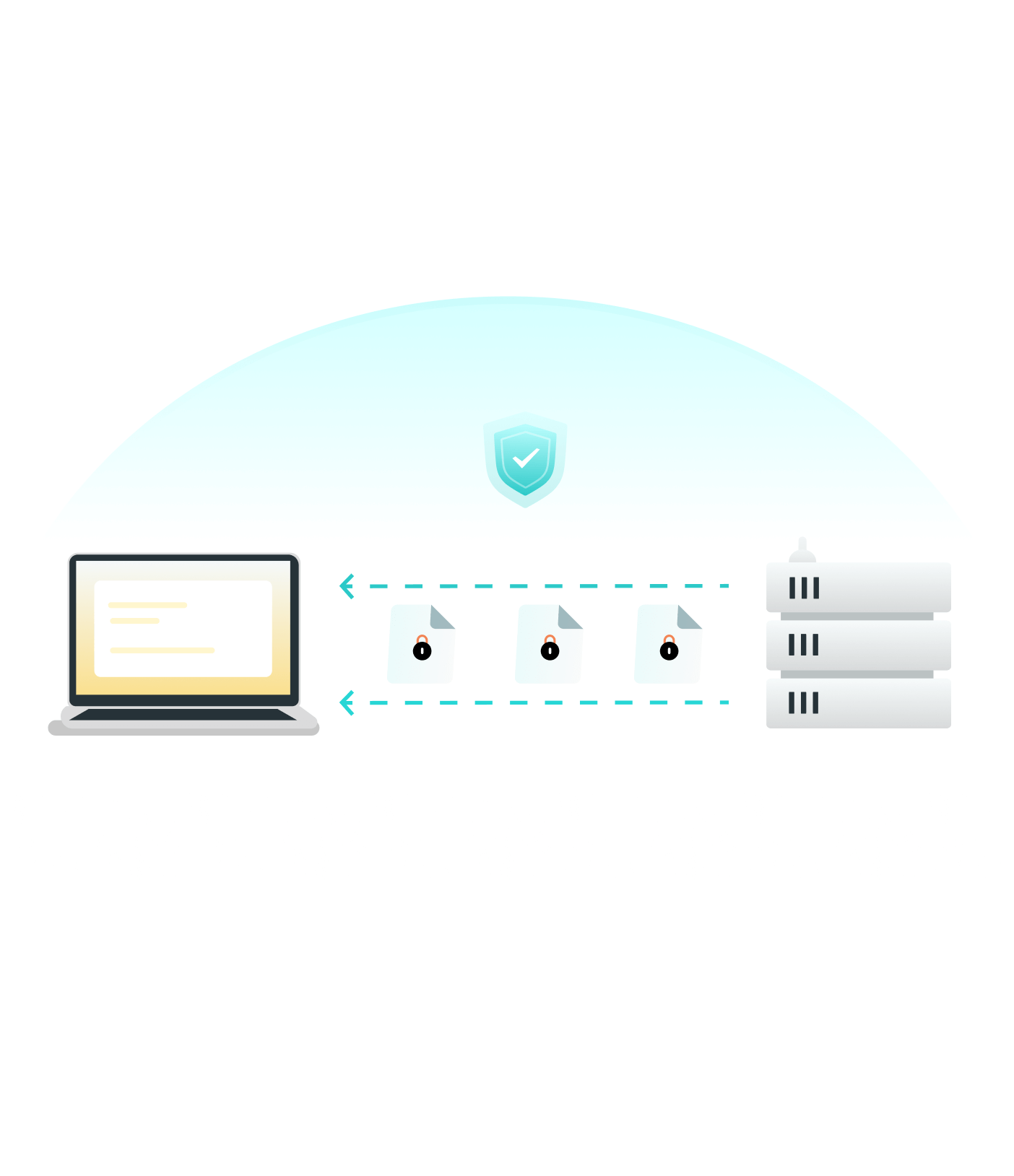
Step 5. Return Path
The VPN server encrypts data from the website and sends it back to you through the tunnel.