Featured Articles
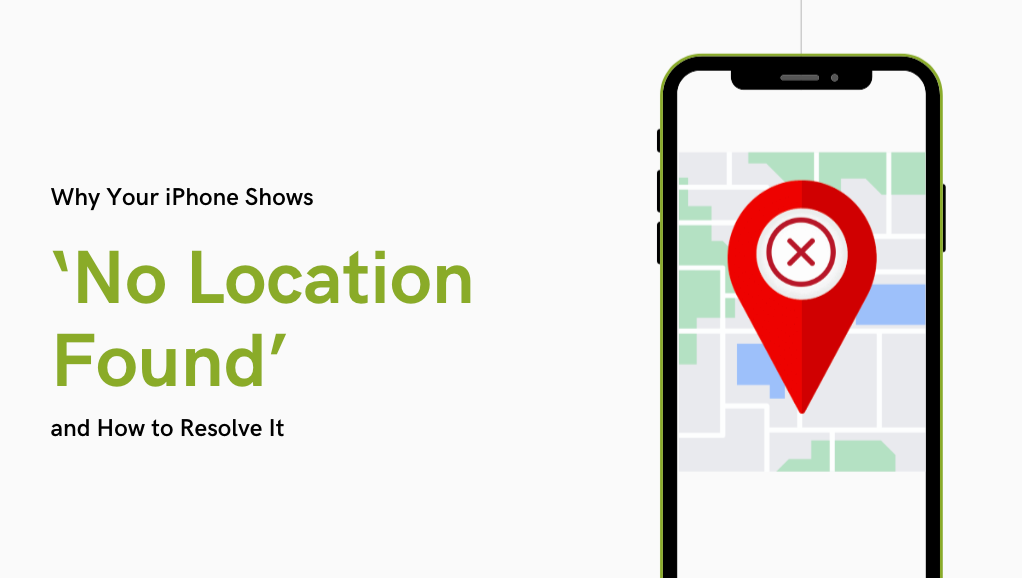
Why Your iPhone Shows “No Location Found” and How to Resolve It
Are you seeing the No Location Found message on your iPhone while using the Find My app to locate a friend’s position? Don’t panic. This isn’t always an issue on your friend’s end. It could be related to factors like GPS signal problems, network issues, or location settings on your device. In this article, we’ll […]

6 Best DNS Servers For Gaming in 2026: Fast and Safe
Choosing the right DNS server can help you avoid lag and disconnections while gaming, make game downloads or updates smoother, and offer you a safer internet environment. Don’t know where to find a suitable one? Check below, we’ll explore the 6 best DNS servers for gaming. TL;DR Here is a quick summary offered for you […]