A Cloud VPN is a secure, cloud-based service enabling remote employees and offices to access internal systems safely, eliminating the need for complex hardware installations and reducing setup time.
In this guide, we’ll explain what a Cloud VPN is, how it works, its benefits and limitations, and how to choose the right one for your team.
💡 Cloud VPN is just one of several VPN types. For a complete overview, see our Types of VPN guide.
Table of Contents
What Is a Cloud VPN?
A Cloud VPN (also referred to VPN as a Service, or VPNaaS) is a cloud-based network service that creates a secure, encrypted tunnel over the internet between remote users and a company’s internal systems or data hosted in the cloud. It allows employees, contractors, and company-owned devices to safely access internal systems, without needing to be physically on-site or using local hardware.
Typically, a cloud VPN consists of 3 parts: VPN gateway, VPN client, and control panel.
VPN Gateway
The VPN gateway builds and secures the encrypted tunnel — the private path your data travels through. Think of the tunnel like a sealed pipe. The gateway decides who can use it and what flows through.
VPN Client
This VPN client is the software installed on your devices. It verifies your identity and talks to the VPN gateway to create a secure tunnel. Without it, the VPN can’t start. Think of it as the key that unlocks your private connection to the company’s systems.
Control Panel
The control panel is where admins manage access — who gets in, how much data they use, and what rules apply.
Because the service is fully cloud-managed, setup is faster, scaling is easier, and ongoing maintenance stays lower. Many providers also offer advanced features like threat detection, multi-factor authentication (MFA), and network segmentation to further enhance security and control.
How Does a Cloud VPN Work?
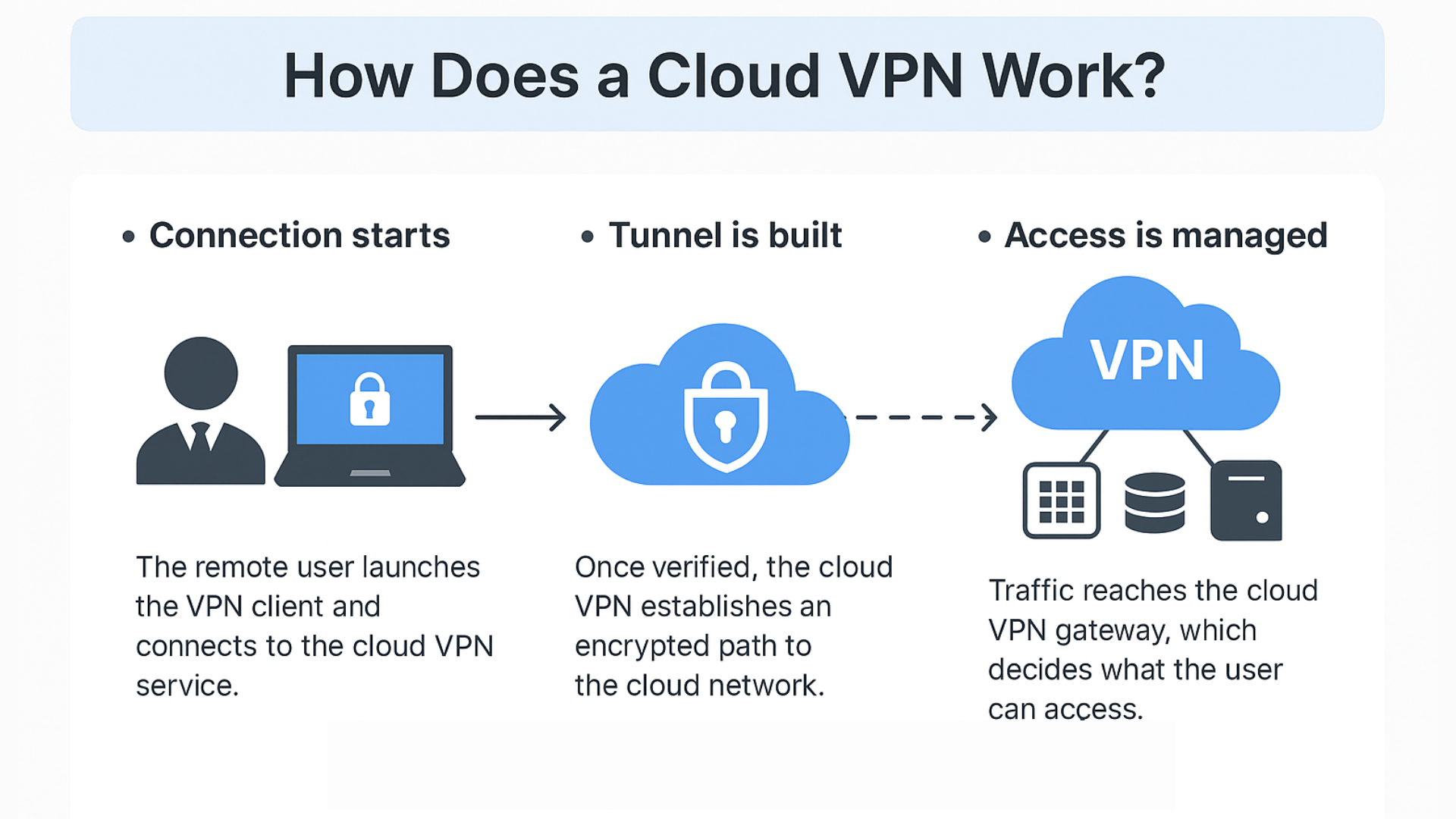
A cloud VPN secures remote access by creating an encrypted tunnel over the internet between a user’s device or office network and the company’s cloud resources. This tunnel protects data as it travels between endpoints, shielding it from interception or tampering.
Here’s a simplified breakdown of the process:
1. Connection starts
The remote user launches the VPN client and connects to the cloud VPN service. The system verifies the device and user credentials — often using MFA and identity providers like Azure AD or Okta.
2. Tunnel is built
Once verified, the cloud VPN establishes an encrypted path between the user’s device and the cloud network. It uses standard VPN protocols like IPsec, IKEv2, or SSL/TLS to ensure all data travels through this private tunnel, safe from interception.
3. Access is managed
Traffic reaches the cloud VPN gateway. Based on the user’s identity and security policy, it decides what systems they can reach — apps, databases, storage — and applies firewall and logging rules.
Cloud VPN Connection Types
To support secure and encrypted access to cloud resources, cloud VPNs typically use two types of connections: remote access and site-to-site.
Cloud-Based Remote Access VPN(Client-to-Cloud)
This setup connects a single user — often working from home, a café, or on the go — to company resources in the cloud. It uses a VPN client installed on the user’s device.
It’s built for flexibility. Remote teams, freelancers, or employees using personal devices (BYOD) use this model to safely access internal apps, databases, or cloud files. The connection point changes based on where the user is.
Think of it like joining a company Zoom call. You don’t need to be in the office, just verified and connected.
Key Question | Client-to-Cloud VPN Answer |
|---|---|
Who Uses It? | Remote employees, contractors, freelancers. |
How to connect? | Initiate a connection through a VPN client on a laptop, mobile phone, etc. |
Where to connect? | Connect to the company’s systems deployed on cloud services such as AWS, Azure, Google Cloud, such as enterprise applications, databases, or file storage. |
Is it a fixed network? | No, the connection point varies with the user’s location. |
Common scenarios? | Remote work, business travel, BYOD (employees use their own devices). |
Site-to-Site VPN(Network-to-Cloud)
Network Cloud VPNs connect an entire office network to cloud-based resources. Instead of logging in per person, the link is built between two networks — like your data center and AWS.
It’s always on. Offices, headquarters, and branch locations use this to access private cloud environments securely, with no need for individual VPN clients.
It’s common in hybrid setups, where companies combine on-prem systems with cloud infrastructure across regions.
Key Question | Site-to-Site VPN Answer |
|---|---|
Who Uses It? | Enterprise IT network administrators, headquarters/branch offices. |
How to connect? | Configure VPN tunnels using routers, firewalls, or VPN gateway devices. |
Where to connect? | Connect to a virtual private cloud (VPC) on the cloud, such as AWS VPC. |
Is it a fixed network? | Yes, usually an office or data center. |
Common scenarios? | Establish a hybrid cloud architecture, connect local data centers and cloud environments, and support cross-regional office network integration. |
Cloud VPN Deployment Models
Beyond connection types, cloud VPNs are also categorized by their deployment models — primarily based on connection reliability and availability. The two most common options are High Availability (HA) VPN and Classic VPN.
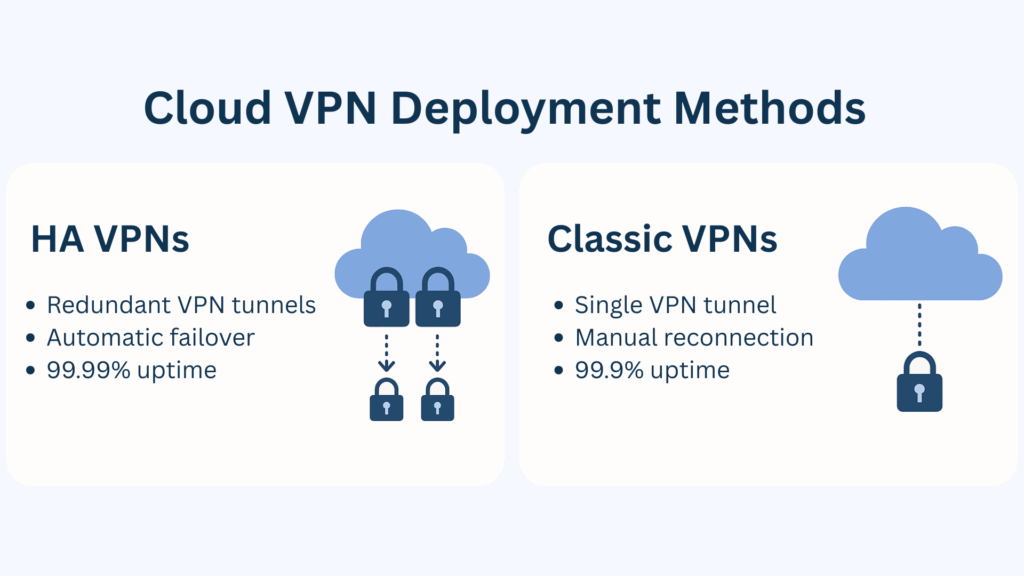
High Availability (HA) VPNs
HA VPN is designed for maximum reliability. It uses two or more redundant VPN tunnels that operate in active-active or active-passive mode. If one connection fails, traffic automatically switches to the backup tunnel — minimizing downtime without manual intervention.
This model typically achieves 99.99% uptime, meaning less than 1 hour of potential disruption per year. It’s a good fit for systems that can’t afford interruptions, like e-commerce, banking, or global operations.
Classic VPN
Classic VPN uses a single tunnel without redundancy. If the connection goes down, it requires manual troubleshooting and reconnection. Uptime usually sits around 99.9% — which could mean 8 to 9 hours of downtime annually.
While less resilient than HA VPN, it’s easier to configure, faster to deploy, and cost-effective, which makes it a practical choice for testing environments or smaller teams with tighter budgets.
In short, HA VPN offers higher resilience at a higher cost, while Classic VPN trades off some reliability for simplicity and affordability. The right choice depends on your business needs, risk tolerance, and availability requirements.
Cloud VPNs vs Traditional VPNs
Now that we’ve covered how cloud VPNs work and the two deployment types, it’s worth asking how they compare to traditional VPNs — especially in areas like scalability, reliability, and long-term cost.
Key Differences in Practice
Area | Traditional VPN | Cloud VPN |
|---|---|---|
Deployment | On-prem appliances or self-managed software | Fully managed, cloud-hosted gateways |
Setup Time | Manual setup, days or weeks to deploy | Quick provisioning via cloud console or API |
Scalability | Limited by physical hardware and IT capacity | Elastic — automatically scales with user or traffic demands |
Maintenance | Requires internal patching, monitoring, and updates | Mostly handled by cloud provider |
Global Access | Centralized, may suffer latency for remote users | Connects users via nearest cloud region |
Cost Model | High CapEx, ongoing maintenance, IT team required | Pay-as-you-go or monthly plans, lower upfront cost |
Security Tools | Depends on in-house configuration | Often includes built-in MFA, DDoS protection, logging |
In short, Cloud VPN fixes many of the pain points that come with traditional setups — hardware dependency, slow scaling, and heavy upkeep. Since it runs in the cloud, setup is quick, access is global, and security features are built-in. For remote or growing teams, it’s a practical way to stay connected and protected.
Benefits & Limitations of Cloud VPNs
While cloud VPNs offer clear advantages over traditional VPNs, they also come with certain trade-offs. For organizations that need autonomous control over infrastructure or highly customized network settings, cloud VPNs may not be the ideal choice. Below, we will analyze the main advantages and limitations of cloud VPNs in detail to help you make an informed decision.
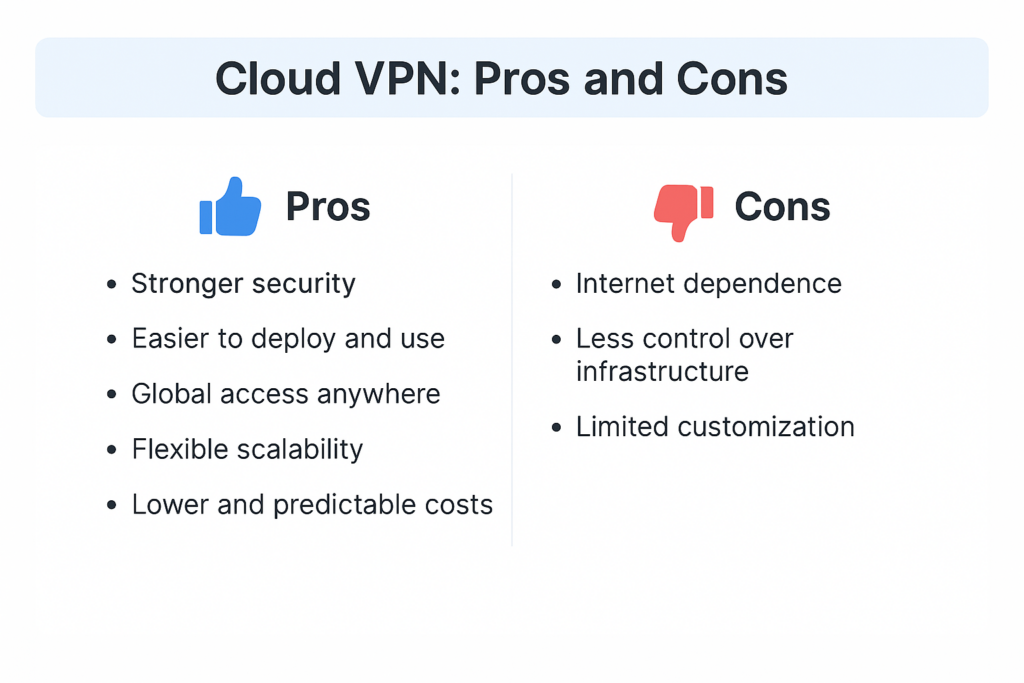
Cloud VPN Benefits
1. Stronger security
Cloud VPNs support strong encryption, multi-factor authentication, and access controls. They also help prevent data leaks with traffic segmentation and built-in monitoring.
2. Easier to deploy and use
There’s no hardware to deploy. Most services work right out of the box with a client app and simple login.
3. Global access anywhere
Users can connect to company systems from anywhere via the nearest cloud node. This setup is ideal for distributed teams and international operations.
4. Flexible scalability
You can quickly adjust capacity as business needs change. No need to worry about hardware limits or fixed bandwidth.
5. Lower and predictable costs
There’s no need to purchase or maintain physical servers when using a cloud VPN. Most services offer on-demand pricing or monthly subscriptions, which helps reduce overall costs and makes budget planning more predictable.
Limitations of Cloud VPN
1. Internet dependence
Since all connections are made through the Internet, if the user’s network is poor, VPN performance may be affected, causing delays or instability.
2. Less control over infrastructure
Using Cloud VPN usually means handing over part of the network security to the service provider, and some enterprises may prefer to fully control it themselves.
3. Limited customization
Some Cloud VPN platforms are not as flexible as traditional self-built VPNs in advanced configuration or personalized rule settings, especially when large enterprises need complex routing control.
Cloud VPN Common Use Cases
According to Mordor Intelligence, the global cloud VPN market is projected to reach $13.05 billion by 2025 — a sign of growing adoption among businesses looking to secure remote access and multi-cloud infrastructure. Here are some of the most common cloud VPN use cases across industries:
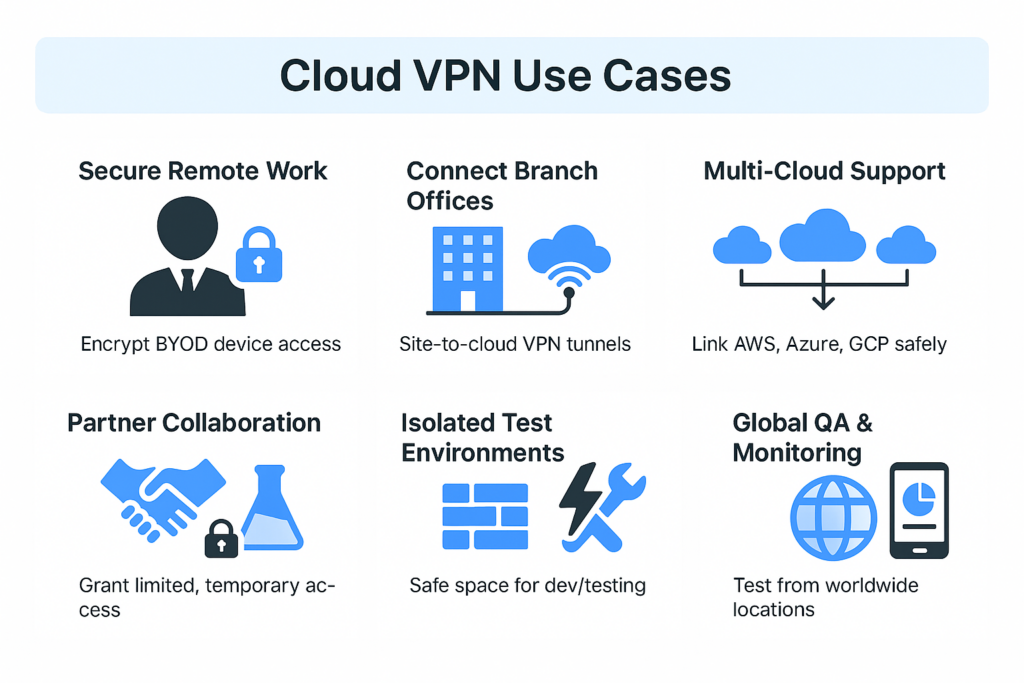
1. Secure remote work and BYOD
Employees and contractors can securely access company systems from any location or personal device — even their own laptops or smartphones (a model known as BYOD, or “bring your own device”). Data stays encrypted, and access is limited to verified users.
For individuals who need secure access without a corporate setup, a free VPN can offer a simple starting point.
2. Connect branch offices
Enterprises with multiple office locations or data centers can use cloud VPNs to establish site-to-cloud encrypted connections to achieve secure data flow between headquarters and branches, just like in the same private network.
3. Support multi-cloud environments
In multi-cloud setups — like using AWS, Azure, and Google Cloud at once — enterprises can use cloud VPNs to secure traffic between platforms, avoid exposing sensitive data to the public internet, and support seamless integration and elastic scaling.
4. Manage external collaboration
You can grant temporary, restricted access to partners, vendors, or project teams — without exposing your full network. Access policies help enforce compliance and limit risk.
5. Isolate development and test environments
Dev teams can spin up secure, isolated spaces for testing code or new features. It reduces the chance of accidental exposure or cross-system issues.
6. Enable disaster recovery
In outages or attacks, a cloud VPN helps keep access online and systems reachable. That’s key for business continuity planning.
7. Test global services
Need to check how your content loads in other countries or regions? Cloud VPNs let teams simulate access from different geolocations for QA, ads, or compliance.
How to Choose the Right Cloud VPN Provider
Not all cloud VPN providers offer the same level of security, performance, or support. To choose the right one for your business, focus on these 6 key factors:

1. Security features
Look for providers that use strong encryption (like AES-256, IPsec), support MFA, offer detailed access controls, and provide audit logs for compliance.
2. Global reach and reliability
If your teams work across regions, choose services with global infrastructure, built-in failover, and SLA-backed uptime — ideally 99.99% or higher.
3. Scalability and integrations
Make the VPN scales with your business and integrates with your existing cloud platforms, identity systems, and DevOps tools.
4. Usability and management
The best platforms offer intuitive dashboards, easy user management, and thorough documentation to reduce IT workload.
5. Support & SLA guarantees
Fast support matters. Look for 24/7 technical help, live chat or ticketing, and clear SLAs to avoid downtime issues.
6. Transparent pricing
Choose a provider with clear, usage-based or flat-rate pricing. Watch for hidden fees, such as limits on bandwidth or user accounts.
Conclusion
Cloud VPNs are a solid option for teams that need secure, flexible access across locations. They simplify remote work, scale with your needs, and work well in multi-cloud setups.
That said, they’re not always the right fit. If you have strict compliance rules, ultra-low latency requirements, or complex legacy systems, something self-managed might work better.
In the end, it’s less about what’s popular — and more about what fits your infrastructure and risk tolerance.
Online privacy made easy
Hide your IP, encrypt your traffic, and take back control of your internet — wherever you are.
FAQs
How does a cloud VPN work?
A cloud VPN creates an encrypted tunnel between your device and cloud services. It verifies your identity — often with multi-factor authentication — then routes traffic securely using protocols like IPsec or SSL. Your data stays protected while in transit.
What is the difference between a cloud VPN and a traditional VPN?
Cloud VPNs run in the cloud and are easier to deploy, scale, and integrate with cloud tools. Traditional VPNs rely on local hardware, take longer to set up, and need more hands-on maintenance.
Is using a cloud VPN secure?
Yes, a cloud VPN is secure when properly configured. It uses strong encryption (like AES-256), supports MFA, and applies access controls. Providers also patch threats regularly. Just ensure users follow good password and device practices.
When should I use a cloud VPN for my business?
If your team works remotely, uses multiple cloud services, or spans different locations, a cloud VPN makes sense. It gives secure access without the need for physical infrastructure.
How do I set up a cloud VPN?
Setting up a cloud VPN is usually simpler than setting up a traditional VPN. First, you choose a cloud VPN provider or use your cloud platform’s VPN service (for example, Google Cloud VPN, AWS VPN, Azure VPN Gateway, or a third-party service).
Then you typically:
1) Log into the provider’s web portal or console
2) Configure a VPN gateway in the cloud (this is the endpoint that your users or offices will connect to)
3) Install VPN client software on user devices (or configure your office router for site-to-site)
4) Distribute credentials or set up identity integration (like linking the VPN to your company’s SSO/identity provider).
The exact steps vary by provider, but most have wizards or documentation to follow. In many cases, it’s a matter of a few clicks to create the VPN tunnel in the cloud, and then users can connect by entering the provided server address and their credentials in the VPN client.
Are there downsides to using a cloud VPN?
It depends on your needs. Cloud VPNs require stable internet and shift some control to the provider. For complex, compliance-heavy environments, a self-managed VPN might be a better fit. But for most teams, the tradeoff is worth it.