SSL VPN has been the way for employees to safely access company resources from home for a long time. But what is it, how does it work, and does it still hold up over time? This guide explains what an SSL VPN is, showing you how to set it up. Listing the security risks of it in recent years and bringing you a comparison between SSL and newer options like IPSec and WireGuard.
Table of Contents
What Is SSL VPN?
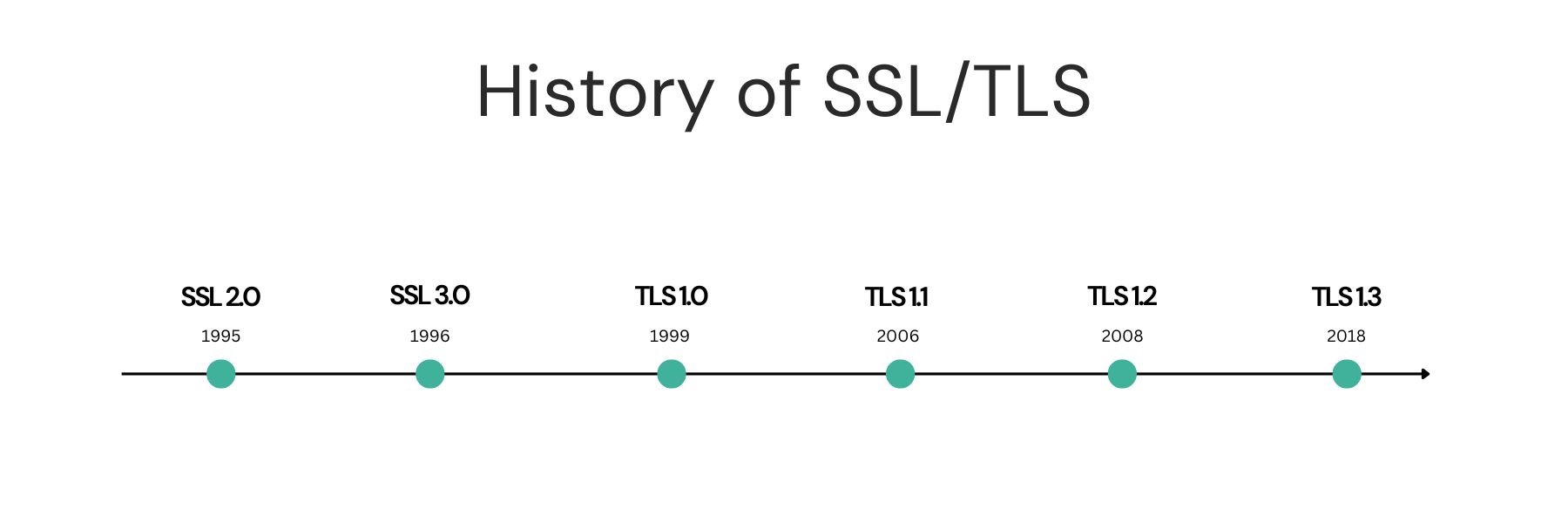
SSL stands for Secure Sockets Layer, a cryptographic protocol designed to provide secure communication over a network. It continuously evolves and upgrades from SSL 1.0 to TLS 1.3 over the years, making both the names SSL and TLS acceptable.
So, what happens when you add VPN (Virtual Private Network) to SSL? An SSL VPN is a technology that uses SSL/TLS encryption protocols to secure the connection between a user’s device and a private network, normally a corporate office. There are basically 2 different types of SSL VPN:
- SSL Portal VPN: Through a secure website (a “portal”), it provides clientless, secure access to particular corporate web applications. Instead of giving access to the entire network, it gives access to specific tools, such as a single file or the email app.
- SSL Tunnel VPN: Typically used with clients such as the WatchGuard SSL VPN Client. By extending the corporate LAN to the distant device, it offers complete network access. Employees can access to all network resources through the encrypted VPN tunnel it builds.

How Does SSL VPN Work?
An SSL VPN works by creating a secure, encrypted tunnel between a user’s device and a private corporate network. The process typically follows these key steps:
1. Establishing a VPN Gateway Connection
Users connect to the VPN gateway by launching a dedicated SSL VPN client application or using a web browser directly.
2. Authentication
Users then verify their identity using credentials. This process often includes multi-factor authentication (MFA) for enhanced security.
3. Tunnel Establishment
Once authentication is complete, the VPN gateway creates a secure tunnel using the SSL/TLS protocol.
4. Secure Access
While the tunnel is active, users can securely access approved internal resources, such as files or applications, as if their devices were directly connected to the corporate network.
5. Encrypted Data Transmission
The tunnel encrypts all data sent between the user and the network, preventing sensitive corporate data from being intercepted.

How to Set Up an SSL VPN for Remote Access?
To set up SSL VPN for remote access, you need an SSL VPN client. Different than a VPN service provider commonly heard for personal online security, SSL VPN clients for remote access here are options like FortiClient, WatchGuard SSL VPN Client, Cisco AnyConnect Secure Mobility Client, and SonicWall Mobile Connect. These clients act as gateways, establishing secure TLS-encrypted connections to your corporate firewall or VPN gateway.
Step 1: Install an SSL VPN client, let’s take FortiGate as an example.
Step 2: Turn on the SSL VPN feature on FortiGate. Then, connect to a user verification system like Microsoft Active Directory or RADIUS for authentication. Next, define access policies by specifying which user groups can access specific applications and creating an IP address range for users, along with firewall rules to control their access.

Image from Fortinet
Step 3: Create a preconfigured installation package that includes the gateway address and any necessary connection settings. Then, install the client on all user devices or provide them with the dedicated URL and their authentication credentials.
The policies you set in steps 2 and 3 determine the user’s access level. After they launch the client and authenticate, they might see full tunnel access or only the authorized applications.
Is SSL VPN Still Trustworthy?
Because of its unmatched convenience, SSL VPN technology has become an essential component of remote access. However, there have been increasing security vulnerabilities of it in recent years.
Throughout 2024 and into 2025, the Akira ransomware gang has actively taken advantage of a known vulnerability (CVE-2024-40766) in SonicWall SSL VPN instances in order to obtain initial access to business networks.
Similar to this, Fortinet’s SSL VPN has serious flaws (like CVE-2024-21762) that state-sponsored organizations have taken advantage of, resulting in serious security breaches.
According to experts, the default LDAP group settings on SonicWall devices can automatically grant excessive permissions to any authenticated user. This could lead to serious security vulnerabilities, giving convenience to cyber attackers.
Also, the UK’s National Cyber Security Centre (NCSC) has pointed out that SSL VPN solutions have a history of serious flaws, such as zero-day vulnerabilities. NCSC has even released guidelines urging organizations to switch from SSL VPNs to more secure options like IPsec (with IKEv2).
Alternative Protocols & Verifying Methods to SSL
Although SSL VPNs revolutionized remote access, their drawbacks and security flaws have forced companies and VPN users to look for more reliable alternatives.
1. SSL VPN vs. IPsec VPN
One protocol that secures communication between networks or clients is IPsec VPN. It is frequently used to link corporate data centers and branch offices, and it is renowned for its robust security.
SSL VPN | IPsec VPN | |
|---|---|---|
Protocol Layer | Application Layer (Layer 7) | Network Layer (Layer 3) |
Primary Use Case | Remote user access | Network-to-network |
Deployment | Clientless (browser) or SSL VPN client | A dedicated client is necessary |
Access Control | Can restrict users to specific apps | All access |
Firewall | Uses common TCP port 443 | Uses unique protocols and ports |
User Experience | Highly flexible | More complex setup |
2. SSL vs. WireGuard
The open-source, contemporary VPN protocol WireGuard was created with ease of use and speed in mind. It is well known for having low latency and quick connection times, which make it perfect for mobile devices and situations where network conditions fluctuate regularly.
SSL VPN | WireGuard | |
|---|---|---|
Protocol Architecture | Based on the mature TLS/SSL protocol | A novel, minimal single protocol |
Key Strength | Granular access control and clientless web access | Raw performance, speed, and simplicity |
Codebase & Auditing | Complex but battle-tested over time | Extremely small codebase, easier to audit for security |
Connection Speed | Slower, due to TLS handshake overhead | Extremely fast, near-instantaneous connections |
Access Control | Built-in to gateway policies (application-level) | Provides full network access; control must be implemented externally |
Ideal Scenario | Enterprise remote work balancing security and flexibility | Site-to-site links, performance-critical users, tech-savvy enthusiasts |
3. Zero Trust Network Access
Though it is not a protocol, ZTNA is dramatically changed the security philosophy from the “trust but verify” model to “never trust, always verify.” ZTNA authenticates every user and every device before permitting access. Because of its increased security, this access control method is becoming more and more popular.
Secure Your Personal Browsing with X-VPN
While SSL VPNs focus on providing secure remote access control for organizations, personal internet security is equally important. That’s where X-VPN comes in. Our solution not only secures your browsing with advanced encryption but also offers the powerful TLS protocol to ensure your data remains private and secure.
100% Free Solution
TLS Protocols Offered
WireGuard Integrated
ZTNA for Ultimate User Privacy
Conclusion
SSL VPN has played a key role in the remote work revolution. However, its vulnerabilities have exposed organizations to risk. Alternatives like IPsec and ZTNA are becoming the norm for enhanced security. Major SSL VPN clients, including FortiClient and Cisco AnyConnect, are also moving to them. Beyond business solutions, download our free VPN for your personal cybersecurity guard.
FAQs
Is SSL VPN Good?
Yes, SSL VPN is a good option for remote access because it’s easy to use. However, whether it’s the best choice depends on the situation. Its past security issues mean it needs careful updates and setup. For many users, modern alternatives like IPsec might be a safer and better long-term option.
Who‘s SSL VPN For?
It is primarily for organizations that need to provide their employees or partners with secure remote access to internal network resources. It is not typically a solution for individual consumers seeking privacy for personal internet browsing.
Is There a Mobile VPN with an SSL Client?
Yes, many VPN solutions offer dedicated mobile apps that use SSL/TLS for remote working. For example, Cisco AnyConnect and FortiClient. Beyond that, there are VPNs like X-VPN that provide a personal-grade solution to protect your privacy with an SSL/TLS protocol.
Is SSL Better Than IPsec?
It depends on your specific needs and use cases. If you need easy, application-specific access, an SSL VPN might be better. If you require full network access and robust security, IPsec could be the way to go.
What’s the Difference Between SSL VPN & Traditional VPN?
SSL VPN is ideal for specific application access, normally used in corporations to control remote access. Traditional VPNs like X-VPN, however, are designed to help personal users change IP addresses, encrypt online data, and access global content.
What’s the Difference between SSL VPN and Port Forwarding?
SSL VPN is focused on providing secure remote access to applications with encryption and user-friendly access, while port forwarding is a method for directing traffic to specific devices or services, often with less security. SSL VPN is generally the safer option for remote access.