DDoS (Distributed Denial of Service) is a distributed denial of service attack, which means multiple attackers launch attacks on one or several targets simultaneously, or one attacker controls various computers located in different places. It can cause website downtime, crash, content tampering, and further serious damage.
DDoS attacks are developed from DoS attacks. However, according to the difference in attack principles and methods, the main common ones are network layer-based DDoS attacks and application layer-based DDoS attacks.
It uses some network protocols and operating systems defects to carry out network attacks using deception and camouflage strategies. The website server is flooded with much information that requires a reply and consumes network bandwidth or system resources. Cause the network or system to be overloaded and paralyzed and stop providing regular network services.
Table of Contents
What Are Network Layer Attacks?
SYN Flood attack
The SYN Flood attack is the most common DDoS attack on the current network, which exploits a flaw in the implementation of the TCP protocol. As a result, the target server is occupied by sending many attack packets with forged source addresses to the network service’s port, thereby preventing other normal users from accessing.
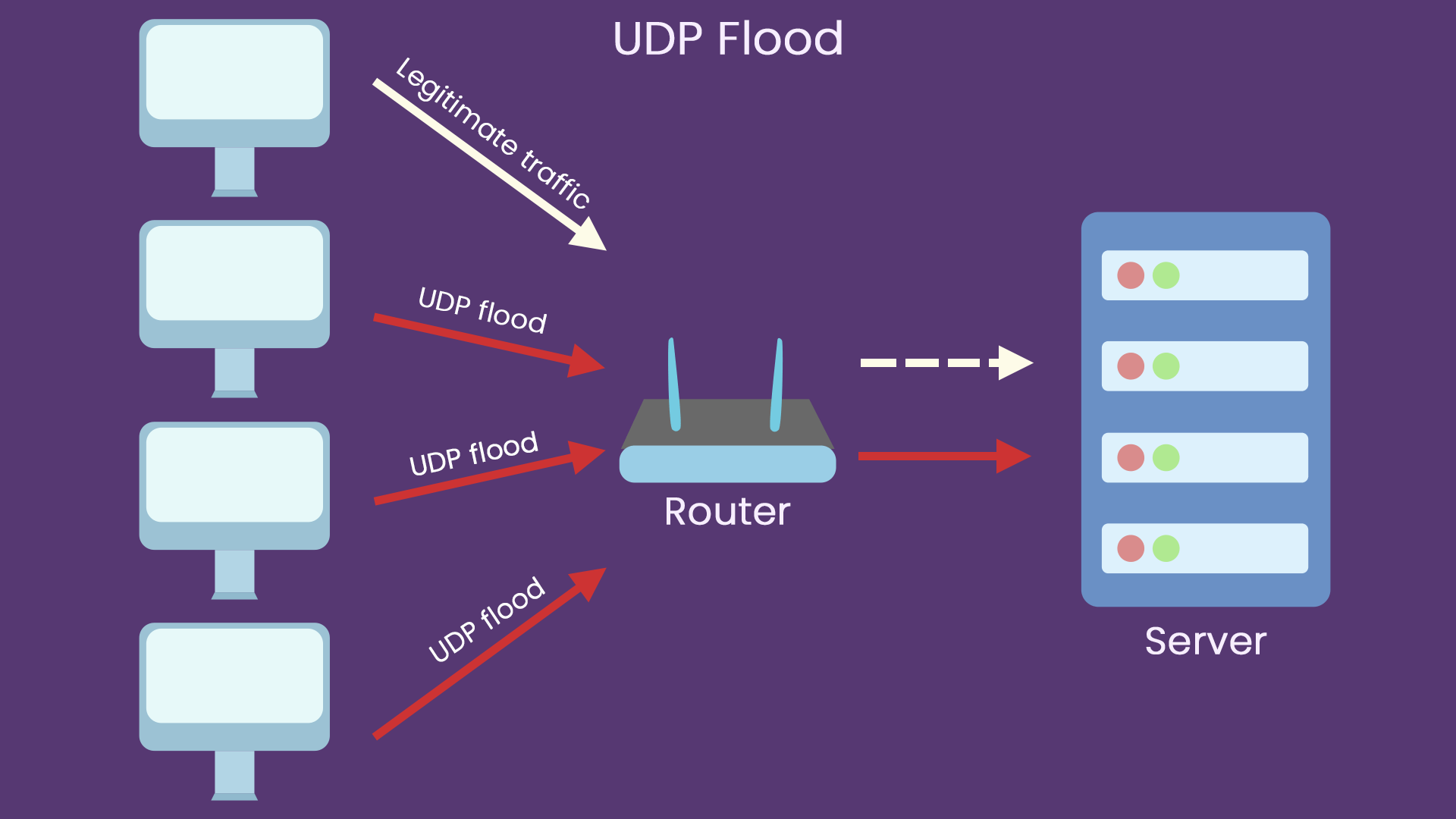
UDP flood attack
UDP Flood is a traffic-based DDoS attack. The principle is to use many UDP packets to impact DNS servers or streaming video servers. Since the UDP protocol is a connectionless service, an attacker can send many small UDP packets with forged source IP addresses in a UDP flood attack.
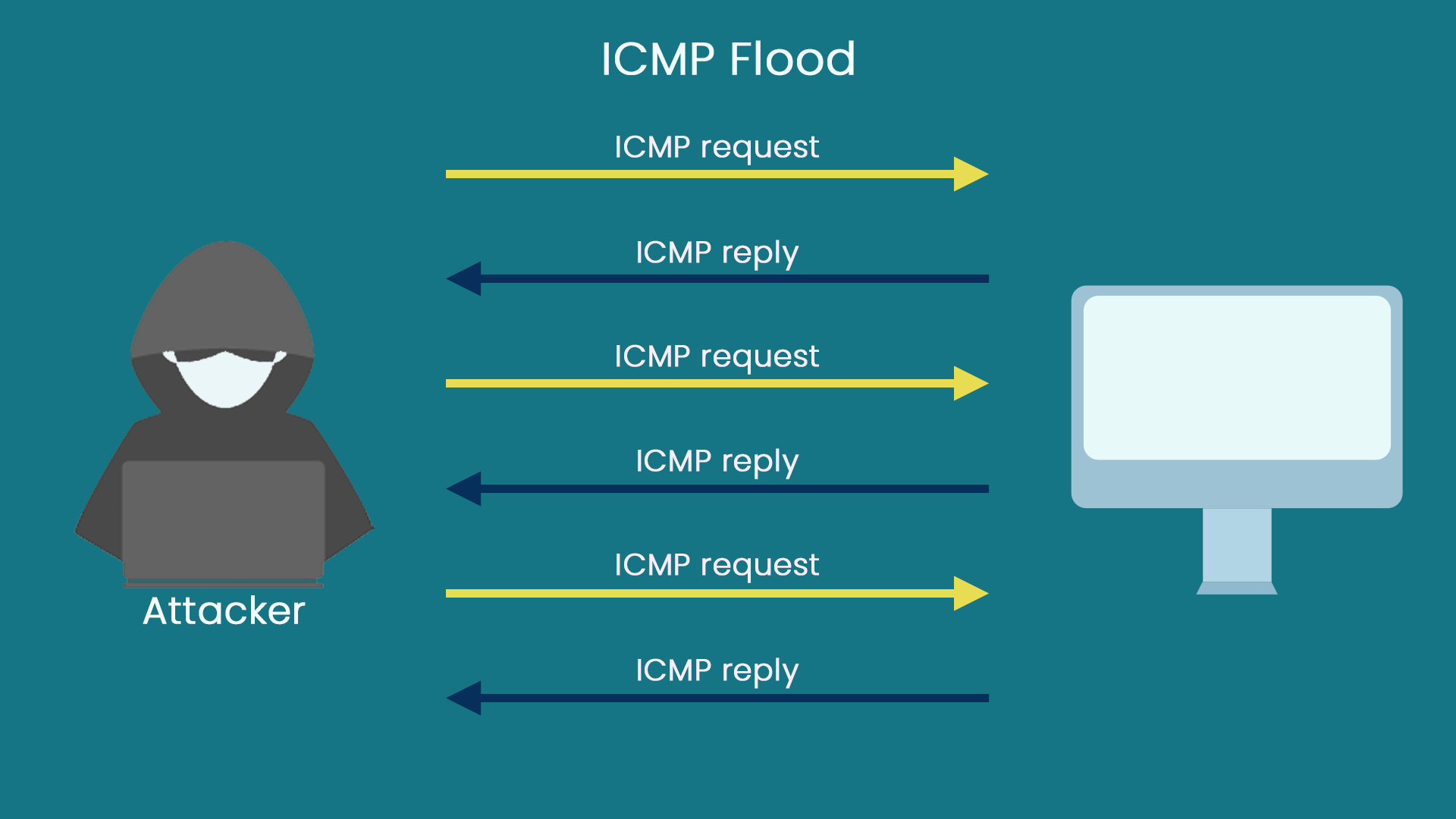
ICMP flood attack
The ICMP flood attack is a traffic-based attack method that uses significant traffic to bring a giant load to the server and affect the standard service of the server.
What Are Application Layer Attacks?
HTTP Get Flood
In an HTTP GET Flood attack, an attacker uses an attack tool to send many HTTP GET packets to the target server, consuming many system resources. As a result, the server resources are exhausted and cannot respond to standard requests.
HTTP Post Flood
In an HTTP POST flood attack, an attacker uses an attack tool to send many HTTP POST packets to the target server, consuming server resources and causing the server to fail to respond to routine requests.
What Are the Differences Between Application-Layer Attacks and Network-Layer Attacks?
Network layer DDoS attacks occur at lower layers, while application layer DDoS attacks utilize higher layer protocols.
The typical attack mode of network layer DDoS attacks is, the attacker uses a fake IP address to control the attack node. The controlled attack node sends many attack packets, such as UDP and ICMP, to the target host.
This attack method takes advantage of the weakness of the TCP three-way handshake mechanism. It consumes many CPU and memory resources after receiving connection requests from non-existent IP addresses. As a result, the attack target cannot provide services to users.
Different from application-layer DDoS attacks, the application-layer DDoS attacks use higher protocols. This collection is based on standard TCP connections and IP packets. Valid TCP connections cannot use fake IP addresses.
How to Deal with DDos Attacks?
The essential factors in DDoS protection are the strength of the defense and the speed at which the attack is defended.
1. Filter unnecessary services and ports
Filter unnecessary services and ports and filter fake IPs on the router.
2. Cleaning and filtering abnormal traffic
Cleaning and filtering out abnormal traffic and prohibiting the filtering of abnormal traffic through rule filtering of data packets, data flow fingerprint detection and filtering, and customized filtering of the data packet content.
3. Distributed cluster defense
This is currently the most effective way to deal with large-scale DDOS attacks. Distributed cluster defense is characterized by configuring multiple IP addresses (load balancing) on each node server.
Suppose a node is attacked and cannot provide services. According to the priority setting, the system will automatically switch to another node, and the server will send the attacker’s data. The packets are all returned to the sending point, making the attack source paralyzed.