IKEv2 is a VPN protocol that creates a fast, stable, secure link—especially on mobile. It handles the “heavy lifting” of encryption, authentication, and reconnects when your connection drops or switches between Wi-Fi and 4G.
If you’ve ever chosen IKEv2 in your VPN app or settings and paused, unsure what it does, you’re in the right place. This guide explains it in simple language, with zero assumption of technical background.
TL;DR: IKEv2 in One Sentence
- IKEv2 is the protocol that lets your VPN “shake hands” with a server securely, agree on encryption rules, and then build the tunnel that protects your data online.
Table of Contents
What Is IKEv2 VPN Protocol?
IKEv2 (Internet Key Exchange version 2) is not a VPN app or service; it’s the ruleset beneath them. It manages how your device and VPN server communicate securely: choosing encryption, verifying identities, and exchanging keys.
Picture the internet as a crowded city. A VPN gives you a private lane through it. Before that lane opens, both sides agree on the rules and who can use it. IKEv2 is the gatekeeper—it verifies IDs, negotiates encryption, and sets the route.
Think of IKEv2 as the gatekeeper: it checks IDs, sets the lock type, and hands out keys. Once it’s done, IPsec steps in to build and run the tunnel carrying your data.
When you connect using IKEv2, your device and the server:
- 1“Greet” each other and agree on encryption methods
- 2Verify identities
- 3Then create the secure channel
All this happens in seconds, behind the scenes. Most major operating systems, iOS, macOS, and Windows already have native IKEv2 support. No extra app needed.
Why Should You Care About IKEv2?
You might ask: now that I get what IKEv2 is, why should I care at all?
Here’s the bottom line: IKEv2 makes your VPN experience smoother. It speeds up data transfer, helps maintain reliability across network changes, and reduces the fuss.
Here’s how:
Quick connections
Fewer handshake steps mean faster starts. You hit “connect,” and it often just works.
Seamless network switching
Thanks to a feature called MOBIKE, switching between Wi-Fi and mobile data won’t drop your VPN tunnel. Ideal for commuters.
Built-in support on most devices
Since iOS, macOS, and Windows support IKEv2 natively, you often don’t need extra apps, just configure and go. Android 11 and higher also have native support with some limitations. Still, a free app like X-VPN offers more features and eliminates the hassle of manual set up.
Battery-friendly for mobile devices
It avoids repeated re-negotiation, so your mobile device doesn’t drain fast while on VPN.
If you prefer VPNs that “just run,” especially on the move, IKEv2 is a strong contender.
How Does IKEv2 Work?
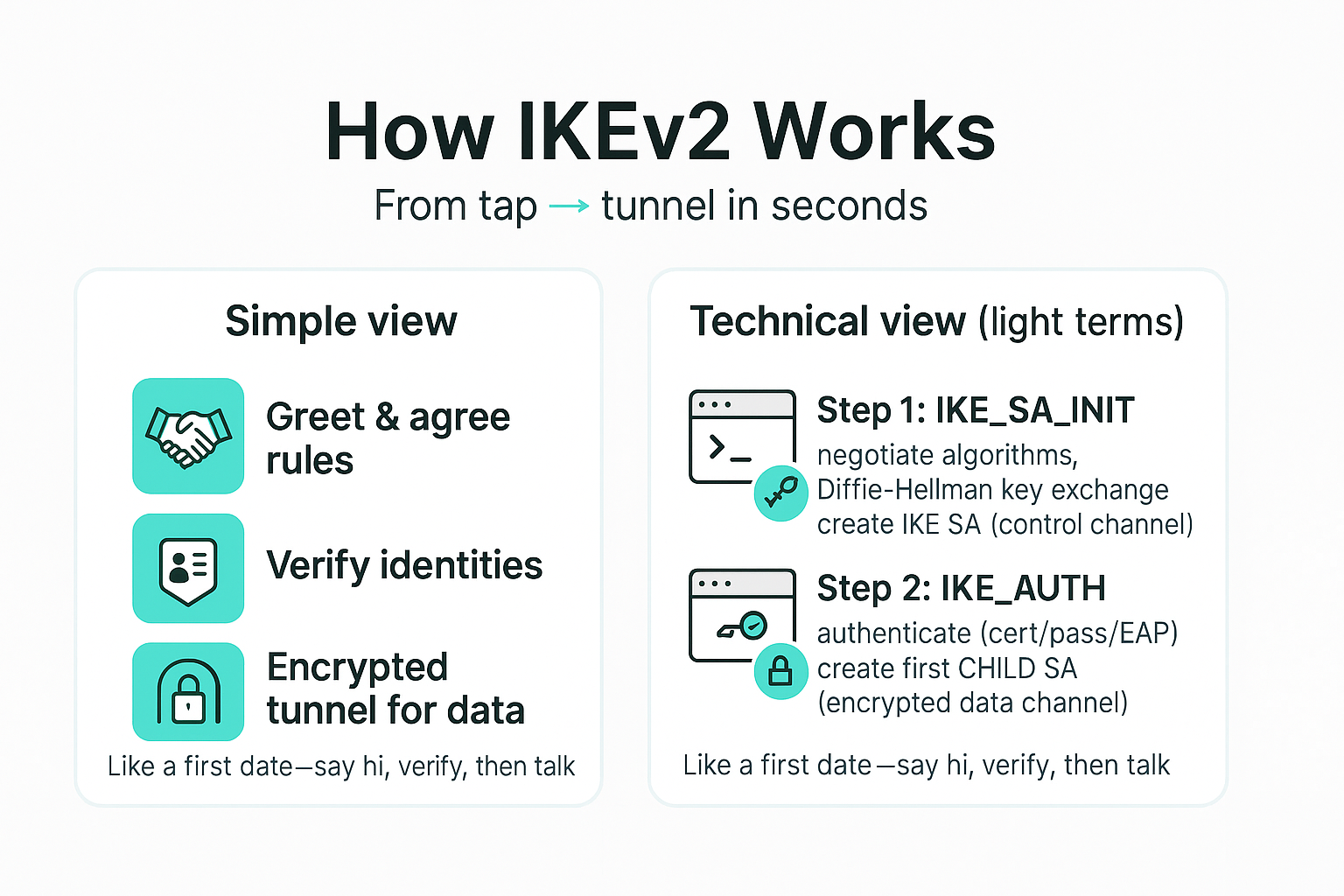
A Simple Explanation (No Tech Background Needed)
When you tap “Connect” on a VPN using IKEv2:
- Your device and the VPN server exchange a greeting, then decide on rules like encryption type.
- They verify identities and then build a secure tunnel for your internet traffic.
Think of it like a first date:
- You say hi and agree where to go
- Verify who each other is
- Then sit down and talk (i.e. data flow)
This all happens in a second or two, fast but crucial for security.
Now Let’s Look at It with Light Technical Terms
IKEv2 uses a two-step negotiation:
Step 1: IKE_SA_INIT
Both sides pick encryption and hashing algorithms, then perform a Diffie–Hellman key exchange. This sets up a “control channel” called IKE SA.
Step 2: IKE_AUTH
They authenticate (with a certificate, password, or EAP), then establish the first encrypted data tunnel, called a CHILD SA.
Ongoing Management
During use, they can create new tunnels (CREATE_CHILD_SA), exchange messages, or rotate keys (INFORMATIONAL) without dropping the link.
You don’t have to memorize the terms. But knowing this process helps you see why IKEv2 is both fast and safe.
Why Is IKEv2 Always Paired with IPsec?
IKEv2 doesn’t operate alone, it’s nearly always bundled with IPsec. Together, they form the backbone of many VPNs: IKEv2/IPsec.
Here’s how they divide the work:
IKEv2 handles negotiation and authentication: deciding which encryption to use, verifying identities, and exchanging keys.
IPsec handles your real data: encrypting your internet traffic and ensuring it arrives intact.
A helpful analogy:
IKEv2 is the security guard who checks your ID and sets the rules,
IPsec is the armored truck that transports your data through the tunnel.
That’s why you’ll often see VPNs referring to IKEv2/IPsec, one builds agreement, the other delivers protection. And most modern systems support this combo out of the box.
Pros and Cons of IKEv2 VPN
Here’s a transparent look: what IKEv2 does well, and where it can struggle.
IKEv2 Pros: Why people love it
IKEv2 Cons: Keep these in mind
IKEv2 Ports and NAT-T: Why 500 and 4500 Matter
Ever wonder why your VPN works at home but not at school or on public Wi-Fi? The answer often lies in ports, and IKEv2 uses two you should know: UDP 500 and UDP 4500.
By default, IKEv2 sends traffic through UDP port 500, which is like knocking on the door. If that door is blocked (common in NAT environments), IKEv2 switches to UDP port 4500 using NAT Traversal (NAT-T). That allows encrypted traffic to pass through routers and firewalls that might otherwise reject it.
If your VPN never connects or gets stuck, chances are ports 500 or 4500 are blocked. You don’t have to change anything yourself, your VPN handles the switch. But for troubleshooting, remembering those two numbers can often solve the mystery.
IKEv2 vs. Other VPN Protocols: Quick Comparison
Not sure whether IKEv2 is the best pick? Here’s how it matches up with its peers:
Protocol | What It Is | Pros | Cons |
|---|---|---|---|
IKEv2/IPsec | Built into most OS; mobile-friendly | Fast, stable, battery-friendly | Fixed ports vulnerable to blocking; closed source |
OpenVPN | Open-source, widely used, highly flexible | Strong encryption, highly configurable | Slower connections, complex setup |
WireGuard | Lightweight, modern protocol | Fast performance, small codebase, battery-friendly/efficient | Config-dependent privacy: key-to-IP mapping; mitigated by rotating/ephemeral keys |
L2TP/IPsec | Legacy protocol, now outdated | Easy to deploy, supported in older systems | Poor performance, considered insecure today |
Bottom line?
IKEv2 works beautifully for mobile users wanting reliable, low-effort VPNs.
OpenVPN is better for flexibility or bypassing strict networks.
WireGuard excels in performance but isn’t perfect for all environments.
L2TP/IPsec is mostly legacy, use it only if you must.
Who Is IKEv2 Best For?
Still undecided? If you fit one of these profiles, IKEv2 might be exactly what you need:
Mobile workers and commuters
Keep your VPN alive even when switching networks.
Business users
Need certificate authentication or enterprise integration? IKEv2 supports it.
People who hate complicated setups
It’s often plug-and-play on supported systems, no extra apps needed.
Travelers and remote users
Reconnect quickly after network changes or interruptions.
If your usage involves mobility and you prefer minimal fuss, IKEv2 deserves serious consideration.

Try X-VPN with the Best VPN protocols
X-VPN uses modern protocols to deliver a smooth, secure connection — great for work, travel, and streaming
IKEv2 Troubleshooting Tips (No Tech Jargon Needed)
Having trouble making IKEv2 work? Try these quick fixes:
Can’t connect at all?
Check your server address, credentials, or certificate. Also, make sure your device clock is synchronized.
Keeps failing?
The server might not support MOBIKE. Try a different server.
Stuck “connecting”?
Your network may block IKEv2’s ports, such as UDP 500 and 4500.
Connected but no internet?
Check DNS settings or split tunneling configuration. Or if you’re having persistent issues and want to temporarily disable the VPN, follow this step-by-step guide to turn off VPN on any device.
Pro Tip: On school, office, or public Wi-Fi, VPN traffic is often blocked entirely. In such cases, try switching to OpenVPN or WireGuard.
So… Should You Use IKEv2?
If you’re on a smartphone, Mac, iPhone, or Windows 10 device, IKEv2 is often your best default bet, it’s fast, stable, and typically ready out of the box.
However, in heavily censored or restrictive networks, IKEv2/IPsec’s common UDP ports 500/4500 (NAT-T) can be filtered or flagged. Obfuscation or a fallback protocol that supports obfuscation (often OpenVPN-over-TLS or WG-over-HTTPS/QUIC) helps reduce blocking.
For most users, though, IKEv2 strikes an excellent balance: speed, security, and simplicity, with minimal setup and solid everyday performance.
A good VPN offers multiple protocols giving you the best of speed, flexibility, efficiency, and privacy.
FAQ
Is IKEv2 a VPN app?
No. IKEv2 is a protocol, the set of rules your VPN app or system uses in the background to establish secure connections.
Is IKEv2 safe?
Yes, when implemented correctly. It supports strong encryption, secure authentication methods, and key rotation. But security also depends on your VPN provider’s infrastructure.
Is IKEv2 fast?
Often yes. IKEv2 uses fewer messages than IKEv1 and, with MOBIKE, can quickly re-establish or maintain sessions when you switch networks. Overall speed depends on the implementation and infrastructure.
What devices support IKEv2?
Most: iOS, macOS, Windows, Android, and some routers. Many have native support, no extra apps required.
Why can’t I connect using IKEv2 sometimes?
Common reasons:
– Network blocks UDP 500 or 4500
– Device clock is off
– Wrong credentials or certificate
– Server lacks MOBIKE support
How does IKEv2 compare to OpenVPN or WireGuard?
– IKEv2: quick, stable, mobile-friendly, but easier to block
– OpenVPN: flexible, bypass-friendly, but slower
– WireGuard: blazing fast and simple, but less mature in some use cases
Can I use IKEv2 for gaming or streaming?
Yes, if your VPN server is strong. The fast connection and low latency make it suitable for gaming and streaming, depending on server location and quality.
Do I need to configure IKEv2 manually?
Usually not. Most modern devices let you just add a VPN profile using your provider’s info. On iPhone and macOS, you can do it in minutes via Settings.