L2TP (Layer 2 Tunneling Protocol) is a VPN protocol that builds a tunnel for your data but does not secure it with encryption by itself. To protect data, it’s typically paired with IPsec, creating what’s known as L2TP/IPsec. This combo lets you build secure virtual tunnels over public networks.
For years, this combination was a popular VPN setup thanks to its broad compatibility. But in 2026, it’s slowly losing ground. Newer protocols like IKEv2 and WireGuard are now favored for their better speed, security, and support on mobile devices.
In this guide, we will explain what L2TP does, how it works with IPsec, and whether it is still the right choice for you today.
Table of Contents
Quick Look at L2TP in One Minute
If you’re short on time, here’s what you need to know about L2TP:
- What it isL2TP (Layer 2 Tunneling Protocol) is a VPN tunneling method. It creates a secure path for data to travel, but it does not encrypt the data.
- Why it needs IPsecL2TP is almost always used with IPsec. L2TP builds the tunnel, and IPsec adds encryption, authentication, and data integrity.
- Where it’s usedCommon in legacy systems, corporate VPNs, and older devices. Built into most OS platforms like Windows, macOS, and Linux.
- Why it’s decliningL2TP/IPsec is slower due to double encapsulation and struggles with network address translation (NAT) and firewall traversal.
- Cutting-edge alternativesIKEv2, WireGuard, and OpenVPN are now favored for their speed, stability, and mobile support.
This combination of L2TP with IPsec is known as L2TP/IPsec. It is still in use today, although it is no longer the go-to choice for new VPN setups.
How Does L2TP Work?
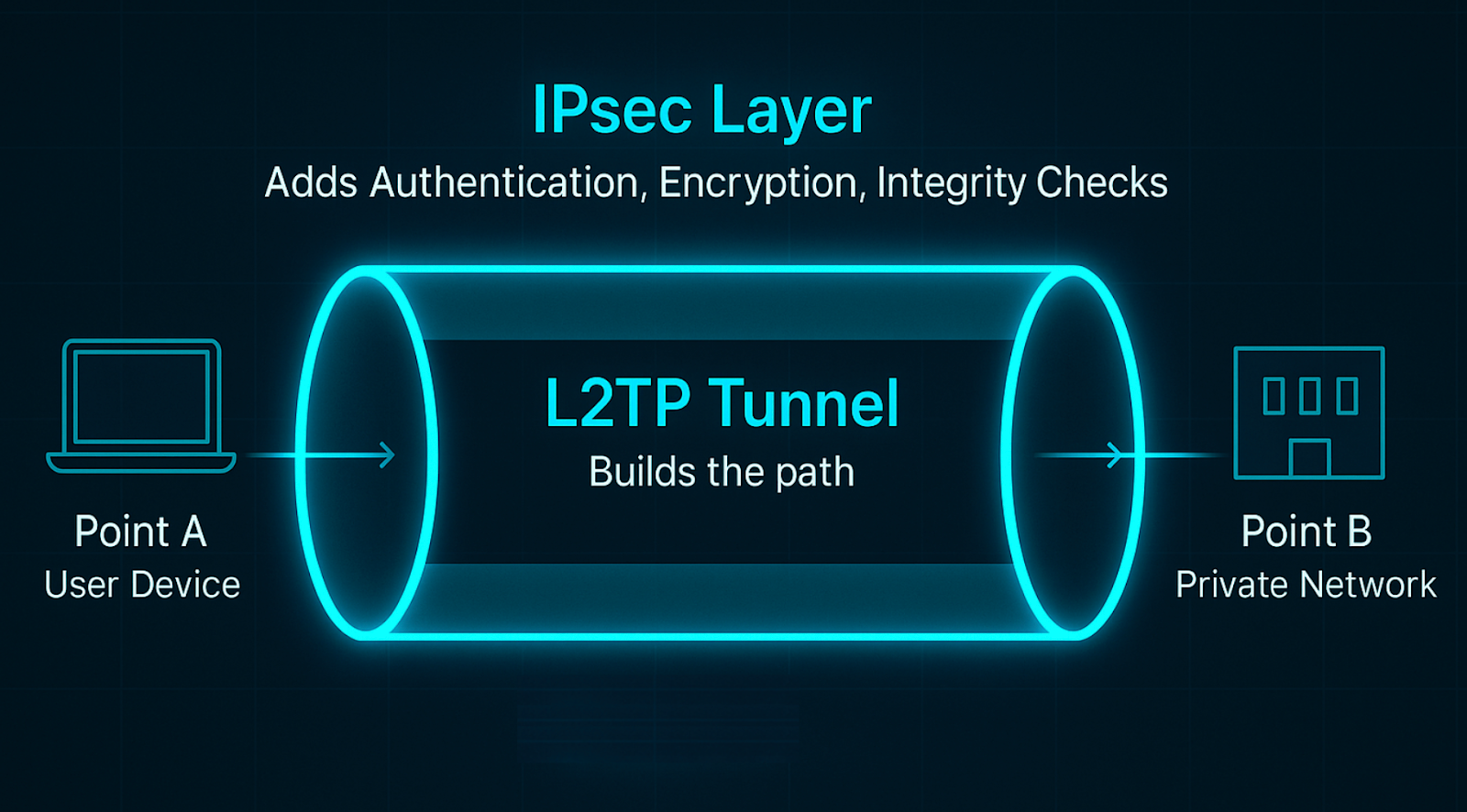
L2TP (Layer 2 Tunneling Protocol) is a VPN technology that creates a virtual tunnel between two networks. It lets your data travel safely from point A to point B across the public internet.
It’s worth noting that L2TP only builds the tunnel. If used alone, it’s like sending an unsealed box through a tunnel that anyone can peek into.
That’s why IPsec is always added:
- Authentication – Confirms your identity.
- Encryption – Hides the data from outside eyes.
- Integrity checks – Makes sure no one tampers with your data.
Together, we call this L2TP/IPsec.
A Real-World Example
Imagine you’re working from home and need to access your company’s internal network, like a file server or office printer. But your connection goes through the public internet, which is shared with millions of users. Anyone could potentially see or tamper with your data.
What’s the solution?
Instead of sending your data without protection, you do two things:
- Use L2TP to wrap the data, like putting it inside a secure tunnel.
- Use IPsec to lock the tunnel, adding encryption and authentication.
This setup creates a VPN tunnel. L2TP builds the tunnel, and IPsec secures it.
Breaking Down the L2TP/IPsec Workflow
So how does the full communication process work? To understand how L2TP/IPsec operates, let’s break it down by roles first:
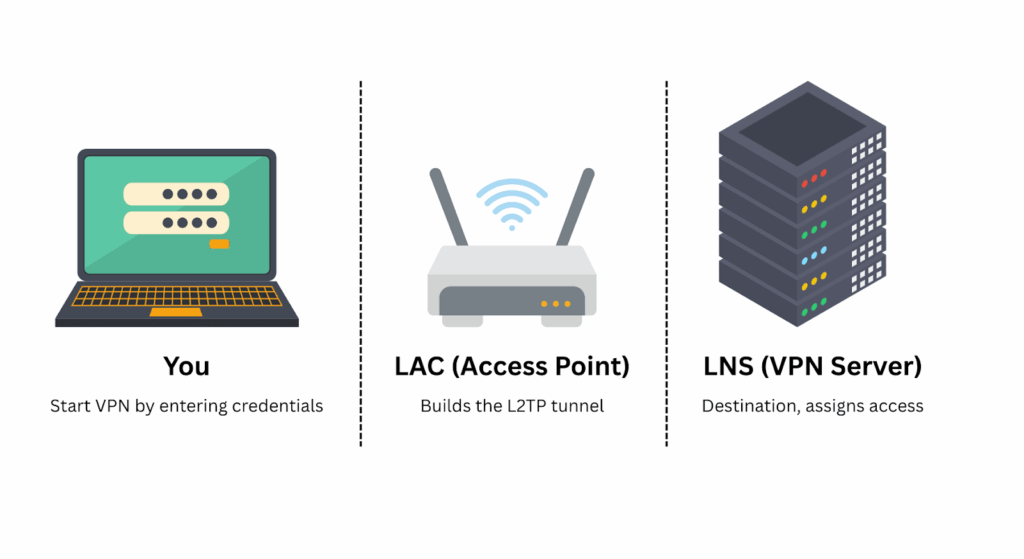
Starting the VPN
You start the process by entering your VPN credentials and clicking “Connect” on your device. Your request is sent through the internet toward the VPN infrastructure.
LAC (L2TP Access Concentrator) – The entry point
This is the first stop for your VPN connection. It might be your home router, your internet provider’s system, or a built-in gateway inside your VPN app. The LAC accepts your request and starts building a virtual tunnel using L2TP.
LNS (L2TP Network Server) – The destination
On the other end is the LNS. This is the VPN server that connects to the private network you want to access. It is often managed by your workplace or VPN provider. Once the tunnel reaches the LNS, it assigns you a virtual presence on that network, similar to receiving an office badge even though you’re working remotely.
Once all the roles are in place, here’s how the full communication process works from start to finish:
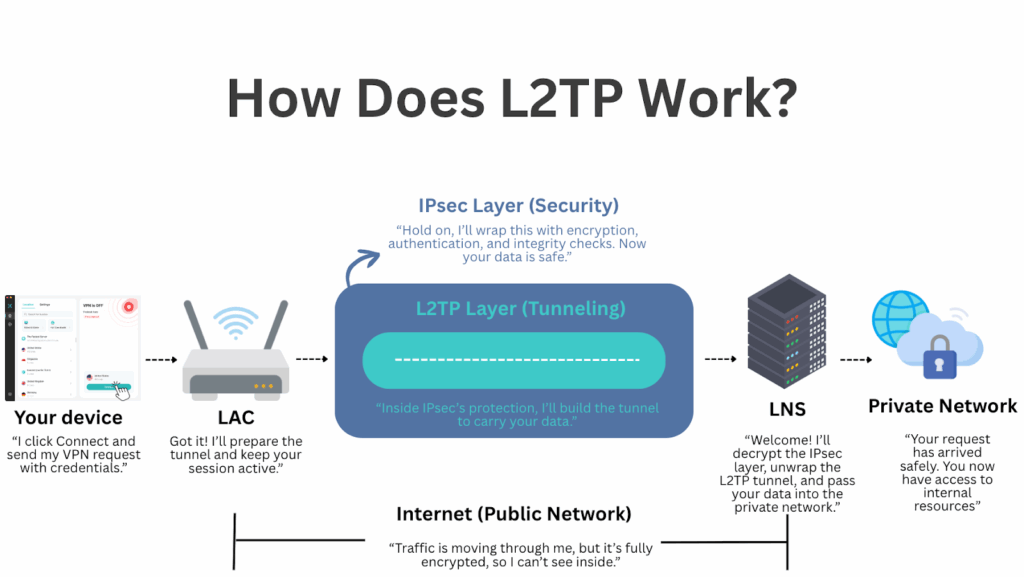
Your Device → LAC → Internet → LNS → Private Network
- You start the connection on your device by entering your VPN credentials. The request goes out over the internet.
- The request reaches the LAC (the access point on your side). The LAC prepares for tunneling and keeps the session state.
- IPsec sets up the encrypted channel to protect the session. This secure layer comes first.
- L2TP builds the tunnel inside that encrypted layer. This tunnel is the path your data will use.
- Once the traffic reaches the LNS, it decrypts the outer IPsec layer, removes the L2TP tunnel, and forwards the data to its destination on the private network.
- Any return data goes back the same way, following the encrypted tunnel in reverse.
Rather than two separate tunnels, L2TP/IPsec uses double encapsulation: L2TP provides the path, and IPsec adds the lock around it. It offers good compatibility and security, but as we’ll see later, it can also introduce speed and connectivity issues.
Is L2TP Secure in 2026?
As mentioned earlier, L2TP alone is not secure, which is why it is usually paired with IPsec to form L2TP/IPsec. So the real question is: Is L2TP/IPsec still secure today?
Still Secure, But Falling Out of Favor
When properly implemented, L2TP/IPsec is still considered secure in 2026. IPsec handles the encryption work by generating secure keys during each session and applying strong algorithms like AES-256 (an industry standard) or 3DES (used in older systems). Even if someone intercepts your traffic, they won’t be able to read the data.
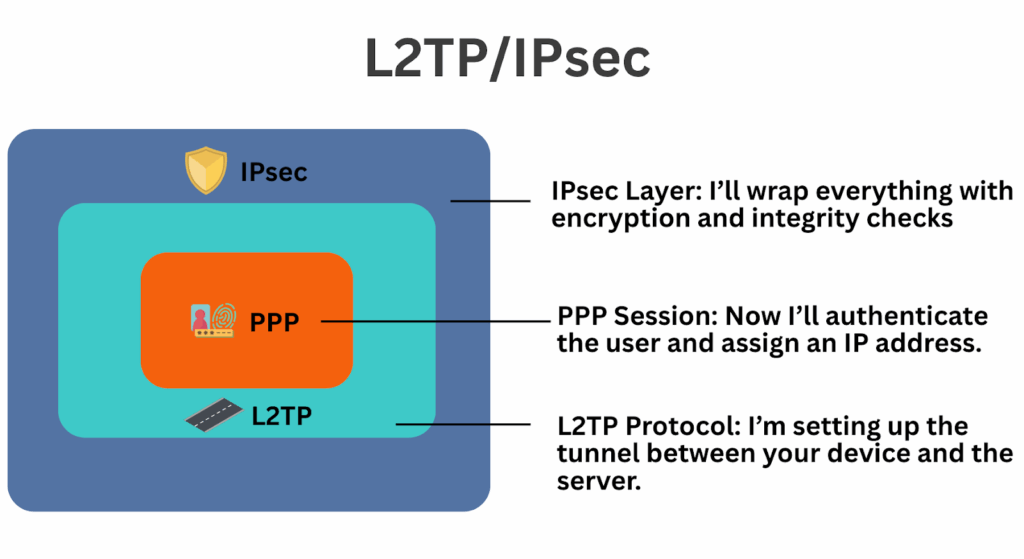
The encrypted connection also includes integrity checks to ensure your traffic isn’t altered or tampered with. These checks apply to both your main data and the control information that manages the connection. This control information is typically wrapped in something called PPP (Point-to-Point Protocol). You can think of PPP as the inner container that holds your data, much like placing documents into a sealed envelope before sending them through the tunnel.
Why Setup Matters
However, the security of L2TP/IPsec depends on the correct setup. Weak pre-shared keys or sloppy configuration can expose the tunnel to attacks. That’s why VPN providers and network administrators stress using strong passwords, complex keys, and precise configuration. Allegations have circulated that intelligence agencies like the NSA may have weakened certain implementations (see discussion here), but the main risk arises when weak passwords or outdated settings are used. With proper deployment, L2TP/IPsec is still safe for most enterprise and personal use cases.
Pros and Cons of L2TP
While L2TP/IPsec still offers reliable encryption, its real limitations today come down to speed and compatibility. Because L2TP/IPsec encapsulates traffic twice, once for tunneling and once for encryption. This double process consumes more device resources and increases overhead, which can result in slower speeds compared to newer protocols.
It also struggles with today’s network environments. L2TP/IPsec depends on several ports (UDP 500, 4500, 1701) and uses the ESP protocol. Think of ports as “doors” that data must pass through. If a firewall closes even one of these doors, the VPN traffic gets blocked or becomes unstable. That’s why L2TP/IPsec often runs into issues on strict networks, public Wi-Fi, or mobile data.
So, we can summarize the pros and cons of L2TP as follows:
Pros
Cons
Therefore, despite its age, L2TP/IPsec is still useful in certain scenarios. It’s a solid option for enterprise site-to-site connections, legacy systems, or environments where built-in compatibility matters more than speed.
However, for personal VPN use in 2026, especially on mobile or restrictive networks, advanced protocols like WireGuard or IKEv2 are often a better fit. They offer faster performance, easier setup, and stronger firewall traversal.
And now, even free VPN services support these advanced protocols, for example, X-VPN lets you choose WireGuard in its free plan, so you don’t have to rely on outdated options like L2TP anymore.
By the way, if you’re still using L2TP/IPsec today, make sure it’s configured correctly and paired with strong encryption settings. Otherwise, it may be time to upgrade.
L2TP vs Other VPN Protocols
Everyone says up-to-date VPN protocols are faster and more reliable than L2TP/IPsec. But what exactly makes them better? And which protocols are leading the way today? In this section, we’ll compare L2TP with newer options like IKEv2, WireGuard, and OpenVPN, so you can see the differences clearly.
L2TP vs PPTP
PPTP is one of the oldest VPN protocols. It is fast because it uses very weak encryption, but that also makes it insecure by current standards. L2TP, especially when combined with IPsec, is much safer. PPTP is now considered obsolete, while L2TP is still used in legacy systems that need basic VPN support.
L2TP vs IKEv2
IKEv2 is newer and highly reliable on mobile networks. It quickly reconnects when you switch between Wi-Fi and mobile data, which makes it ideal for smartphones and laptops. Unlike L2TP, which only adds tunneling on top of IPsec, IKEv2 is natively part of the IPsec framework, giving it tighter integration and stronger security handling. For mobile users, IKEv2 is usually the better choice.
L2TP vs OpenVPN
OpenVPN is open-source, very flexible, and can run on almost any port, including TCP 443, which helps it bypass firewalls and censorship. L2TP relies on fixed ports and protocols that are often blocked. Both are secure, but OpenVPN generally offers better adaptability in restrictive environments.
L2TP vs SSTP
SSTP, created by Microsoft, uses SSL/TLS to provide strong encryption and easy firewall traversal. It works smoothly on Windows systems but has limited support outside that ecosystem. L2TP is built into more platforms overall, but SSTP may be more reliable for Windows-only deployments.
L2TP vs WireGuard
WireGuard is lightweight, extremely fast, and built on modern cryptography. Its simple design reduces overhead, makes it easier to audit, and improves performance. Compared to L2TP, WireGuard offers faster speeds, smoother performance, and simpler configuration. Many experts now view WireGuard as the default choice today, while L2TP is mainly kept for legacy or enterprise compatibility.
Comparison Table
Protocol | Speed & Performance | Security Level | Firewall Traversal | Platform Support | Best Use Case |
|---|---|---|---|---|---|
L2TP | Slower (double encapsulation adds overhead) | No encryption by itself, secure only when paired with IPsec | Weak (fixed ports often blocked) | Built into most OS (Windows, macOS, Linux, Android, iOS) | Legacy systems, enterprise compatibility |
PPTP | Very fast | Insecure (broken encryption) | Poor | Widely supported but obsolete | Not recommended |
IKEv2 | Fast, stable on mobile | Strong, fully integrated with IPsec | Moderate | Supported on most OS, excellent on mobile | Mobile users, roaming devices |
OpenVPN | Moderate to fast | Very strong (SSL/TLS, community-audited) | Excellent (runs on any port, TCP/UDP) | Needs third-party client | Secure personal VPNs, overcome restrictions |
SSTP | Moderate | Strong (SSL/TLS-based) | Strong on Windows | Native to Windows, limited elsewhere | Windows-focused deployments |
WireGuard | Very fast | Very strong (advanced cryptography) | Good (UDP only, but flexible) | Cross-platform, lightweight | Modern default choice for speed and security |
Final Takeaway
At the end of the day, L2TP doesn’t bring much to the table anymore except its built-in availability on most operating systems. That’s fine if you’re stuck with legacy gear or need compatibility, but VPN providers and most users have already moved on. Today, protocols like IKEv2, OpenVPN, and WireGuard give you the speed, reliability, and security that L2TP simply cannot match. If you’re choosing a VPN in 2026, it makes far more sense to go with a state-of-the-art service like X-VPN, which supports these protocols and works seamlessly across devices.

FAQs
What is L2TP?
L2TP, short for Layer 2 Tunneling Protocol, creates a pathway for your data to move across the internet. On its own, it doesn’t provide encryption. That’s why you’ll usually see it paired with IPsec, a security layer that locks down the tunnel. Together, they’re called L2TP/IPsec.
Does L2TP encrypt data?
L2TP only establishes the tunnel but doesn’t hide the contents within it. To protect the privacy of information, L2TP is almost always used in conjunction with IPsec. IPsec handles encryption, authentication, and integrity checks, ensuring the entire VPN connection is secure enough for business or personal use.
Which ports does L2TP use?
L2TP relies on UDP 1701 for tunneling. When used with IPsec, L2TP also requires UDP 500 for setting encryption keys, UDP 4500 for NAT traversal, and ESP (protocol 50) for transmitting encrypted traffic. If one of these is blocked by a firewall, the VPN may not connect.
Is L2TP VPN good?
This depends on your specific needs. It can still be useful if you’re using older systems, an enterprise setup, or require a protocol built into most operating systems. That said, newer protocols like WireGuard or IKEv2 tend to be faster, easier to configure, and more reliable in restricted network environments. For most users in 2026, these protocols commonly used now are generally the smarter choice.