A VPN is powerful, but a tunnel is not a fortress. It encrypts traffic and swaps your public IP address for the VPN server’s IP, disguising your location and securing data. Despite those protections, some apps and system services can still route data around the edges to gather information you might not want to share.
When I had that realization, several questions followed. What are the risks, what slips past, and how can I protect myself online while still enjoying the apps and websites I need to access?
Table of Contents
Quick Answers and Easy Solutions
Trackers take advantage of DNS and WebRTC leaks, partial IPv6 coverage, loose split-tunneling, and analytics kits to identify you. The solutions are surprisingly simple once you know what to look for. A two-minute leak check helps prevent problems before joining a new network. Adding an obfuscated mode like X-VPN’s Everest protocol, can go a long way toward protecting your privacy with minimal effort. There’s more to the story, though, and the details matter.
What a VPN Covers, and What It Cannot
A VPN wraps your traffic in an encrypted tunnel to a server operated by your provider. That prevents local spying and stops Wi-Fi operators from reading content or tagging your activity to your home address. A VPN offers data privacy and IP masking, but not a full identity reset.
A VPN doesn’t blind the accounts you log into. If you sign in to a social network or streaming service, that company still knows it’s you. A VPN can’t delete device or browser fingerprints, either. Subtle details like screen size, fonts, codecs, and how your browser handles media can form a stable profile, particularly if your settings differ from most others. Treat the VPN as a foundation, then harden the browser and app layer on top.
The Common Bypass Paths
Most bypasses are the result of configuration choices or system design, not an encryption failure.
DNS (Domain Name System) can take a detour when the operating system or a particular app insists on its own resolver, which exposes what you look up, even if page content remains encrypted. Browsers and in-app webviews may reveal addresses via WebRTC, a real-time content protocol for video calls.
On networks that lean toward Internet Protocol version 6 (IPv6), traffic can slip outside the tunnel if your provider only routes IPv4. Split-tunneling (bypassing the VPN for selected apps and services) adds convenience for printers or local dashboards, yet it is also a ready-made escape route for sensitive data.
Some mobile apps include analytics or crash reporters that call home through hardcoded endpoints or alternative transports. Apps have access to permissions that aren’t available in most browsers.
Finally, captive portals and early boot sequences can trigger a few requests before the VPN connects, especially on hotel or café Wi-Fi.

Trackers Don’t Need Your IP
Trackers operate above the network layer, which means IP hiding alone will not stop them. On phones and tablets, advertising identifiers let apps and ad networks track activity even when your address changes. The best solution is to reset those IDs and reduce ad personalization where possible.
Analytics kits measure installations and sessions, profiling your device model, locale, motion sensors, and network hints, none of which depend on your home IP, so even VPN-enhanced privacy needs a little help from app settings and browser hygiene.
Fingerprints can emerge from small clues, but you can minimize this by keeping extensions lean, blocking third-party cookies, and using different profiles for some tasks. Location leaks aren’t limited to the network either. GPS, Bluetooth beacons, nearby Wi-Fi names, and photo metadata can reveal where you are. Review location permissions regularly and exclude location data when possible before sharing images.
iOS and iPadOS Protection Tips
iOS doesn’t have an option for an always-on VPN for consumer devices, but a symbol appears at the top right of the screen when internet traffic is protected via a VPN. Look for this indicator to ensure your data is encrypted and your location is hidden. To avoid competing tunnels, turn off iCloud Private Relay and the “Limit IP Address Tracking” option on the Wi-Fi network you’re using when you rely on a third-party VPN.
The easiest way to cover most leaks is via a good VPN service. Use a kill switch if your VPN provider supports it. This closes gaps during network changes and device wake events, so background services are less likely to bypass the tunnel.
Apple offers a powerful tracking blocker for iPhone and iPad apps. If you switch off Allow Apps to Request to Track in privacy settings, apps won’t prompt you for tracking permission, and can’t access the advertising identifier. That cuts down cross-app profiling that a VPN can’t stop.
App permissions often allow too much access. Trim permissions that could leak your personal information, especially Location, Local Network, and Bluetooth. Finally, use in-app browsers cautiously. If you need to sign into an account, use Safari or another trusted web browser that restricts WebRTC to the VPN route.
Android Guardrails That Matter
Use a VPN to take care of the most critical privacy issues. Use Android’s Always-on VPN plus Block connections without VPN, so online communication is blocked if the tunnel drops. You’ll find both options under Settings > Network & internet >VPN, then the gear for your VPN.
Manufacturers use different terminology, so “Block connections without VPN,” could be called “VPN lockdown” or “Block non-VPN connections.” If you still can’t find it, use the VPN app’s kill switch and look for a key symbol next to the Wi-Fi or cellular connection, which indicates your data is encrypted.
Let the VPN manage DNS to prevent leaks. Ensure only trusted apps have split-tunneling enabled to avoid an unexpected bypass. Reset the Advertising ID in Google > Ads (or Privacy >Ads) periodically to reduce cross-app tracking.
Watch out for unsupported protocols when debugging oddities. Some apps use QUIC over UDP. If a service behaves strangely, check whether your VPN handles QUIC or offers a toggle to prefer TCP for stability. X-VPN supports QUIC to maintain stable connections when networks change without leaking data.
Windows and MacOS Security Steps
You can plug most leaks with a VPN. Let your VPN manage DNS and check that it supports IPv6. If not, temporarily disable IPv6 until your provider adds full coverage.
If you don’t use a VPN with a kill switch, add firewall rules that block traffic when the tunnel is down. Most good VPNs include a kill switch option. If yours doesn’t, you should look for a better solution.
Control WebRTC in the Windows browsers with free extensions like uBlock Origin or Google’s WebRTC Network Limiter. Apple already limits IP leaks via WebRTC in macOS Safari.
When you connect a Wi-Fi hotspot with your laptop or MacBook, and it requires accepting terms or making a payment, that’s called a captive portal. Even if you have to sign into a portal first, you can still protect yourself by connecting the VPN afterward, then rechecking your public IP and DNS to confirm your VPN is working (instructions below).
Browser and App Hygiene That Pays Off
Keep extensions to a minimum, isolate social networks and shopping in a separate profile or container, and block third-party cookies to reduce cross-site tracking. Fewer moving parts means fewer leaks.
When you have the option, choose websites and web apps over installed apps when possible. Many vendor apps bundle extra analytics that are more difficult to block. A website in a secure browser comes with good safety defaults and allows easy security upgrades.
When you’re finished on a website, log out of your account. Closing a browser tab or window doesn’t reset cookies and tokens, but signing out does, helping break any data and activity trail.
How to Test Your Setup in Two Minutes?
Connect to the VPN, visit any IP check page, and make sure it shows the VPN server location rather than your home or café network. Confirm the IP address before anything else, since your public IP is the easiest way to connect online activity to you.
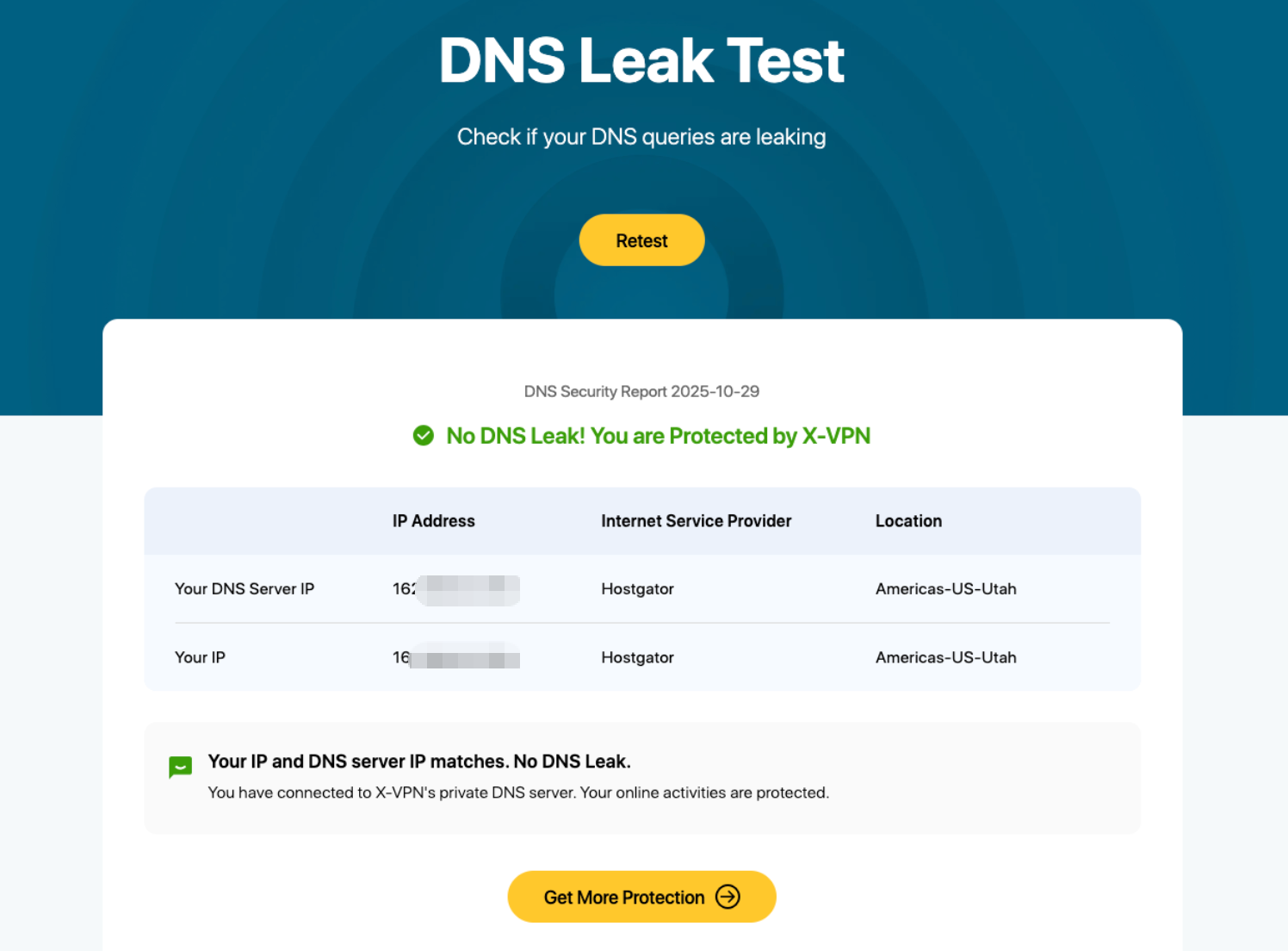
Run a DNS leak test and compare the results. If you see your internet provider’s DNS, your system is not sending queries through the tunnel. Let your VPN handle DNS or align private DNS with the VPN route. X-VPN’s free DNS leak test makes this simple.
Check WebRTC candidates. Use a WebRTC test and confirm that any reported IPs match your VPN exit. If you see a local or home IP, restrict WebRTC to the VPN interface.
Verify IPv6 behavior. If your network offers IPv6, check that the VPN handles it cleanly. If not, disable it until your provider supports it.
X-VPN’s mobile app includes all these tests in the Security Tools tab, making it even easier to check for leaks when you use iOS or Android.
Retest after updates. Major OS or browser updates can reset privacy preferences. A two-minute check prevents weeks of silent leakage.
VPN Features That Reduce Bypass Risk
A VPN is an essential tool for securing your connection, but some apps are better than others, and a paid subscription is almost always safer than a free app.
A kill switch is a must-have feature that blocks connectivity if the tunnel drops, and stops background services and personal data from escaping during reconnection. X-VPN’s kill switch overview explains why automatic cut-offs are crucial for protection..
Obfuscation helps on restrictive or managed networks. If a café, hotel, or campus meddles with VPN traffic, an obfuscated mode can disguise the connection so it blends in with regular web traffic.
Per-app VPN rules are powerful when used sparingly. However, you should limit split-tunneling to low-risk local services. The fewer exceptions you have, the fewer routes a bypass can take.
Full IPv6 and robust DNS handling are quite wins. When your provider properly supports both stacks and carries DNS inside the tunnel, most accidental leaks disappear.
Limitations to Keep in Mind
A VPN cannot anonymize accounts tied to your real identity. It blinds the network path, not the account relationship. Fingerprinting can still connect sessions across time. Captive portals and system services may briefly talk outside the tunnel, although always-on plus a kill switch keeps that window short.
If you’re unfamiliar with encryption and tunnels, you might want to check out our guide to how a VPN works, which sets the stage without overwhelming you with jargon.
Step-by-step Checklist
Turn on the kill switch and confirm your VPN service is running. This blocks internet activity if anything interrupts the tunnel.
- Verify DNS and WebRTC with a two-minute leak check. If there’s a problem, install updates, reset the VPN and test again..
- Let your VPN manage DNS so data flows through the tunnel.
- Review split-tunneling. Don’t bypass the VPN unless you must and limit personal data when you do.
- Reset ad IDs to reduce profiling, and trim app permissions to limit location, network, and Bluetooth access to the essentials.
- Harden the browser. Keep extensions lean, isolate social sites, and block third-party cookies by default.
In a Nut Shell
Treat your VPN as a security and privacy foundation, then shore up the doors and windows. The main bypass routes are well-known, and the countermeasures are simple: lock down DNS, align IPv6, keep split-tunneling tight, and verify WebRTC. Do that, and most apps and trackers have a much harder time stepping around the tunnel. Browser extensions or hardened browsers add a second layer of tracker blocking. The result is a quieter, more private internet that stays practical for daily use.
FAQs
Do I still need tracker blocking if I already use a VPN?
Yes, because they defend different layers. A VPN encrypts traffic and hides your source IP, while tracker blockers disrupt analytics SDKs, third-party cookies, and fingerprinting scripts that operate inside the app or browser.
Can I stop WebRTC leaks without breaking video calls?
Usually, with careful settings. Restrict WebRTC to the VPN interface or allow proxy candidates while blocking direct local candidates, then test your meeting apps to confirm call quality and connectivity.
Should I turn off IPv6 to avoid leaks?
Choose a VPN that supports IPv6 cleanly. If your provider does not, disabling IPv6 can prevent exposure, but the long-term fix is choosing a service that handles both IPv4 and IPv6 through the tunnel.