Distributed Denial of Service (DDoS) attacks are among the most disruptive threats on the internet. They can take down websites, flood servers, and cut off access to online services within minutes. What’s most disturbing is that they’re easy to launch and hard to stop. A DDoS attack can target anyone: businesses, gamers, and individuals, overwhelming networks until everything grinds to a halt.
Understanding how these attacks work and how to prevent them is the first step to staying safe online. Let’s look at what DDoS attacks are, how they spread, and what you can do to shield your devices and data from them.
Table of Contents
The Anatomy of a DDoS Attack
A DDoS (Distributed Denial of Service) attack floods a target with fake internet traffic until the system can no longer handle legitimate requests. The “distributed” part refers to the fact that the attack comes from thousands of devices spread worldwide, all controlled remotely by an attacker.
Imagine trying to drive home, but every road is jammed with identical cars driving in circles, all programmed to block your path. That’s what a DDoS does to a network, clogging every available lane until nothing else can get through.
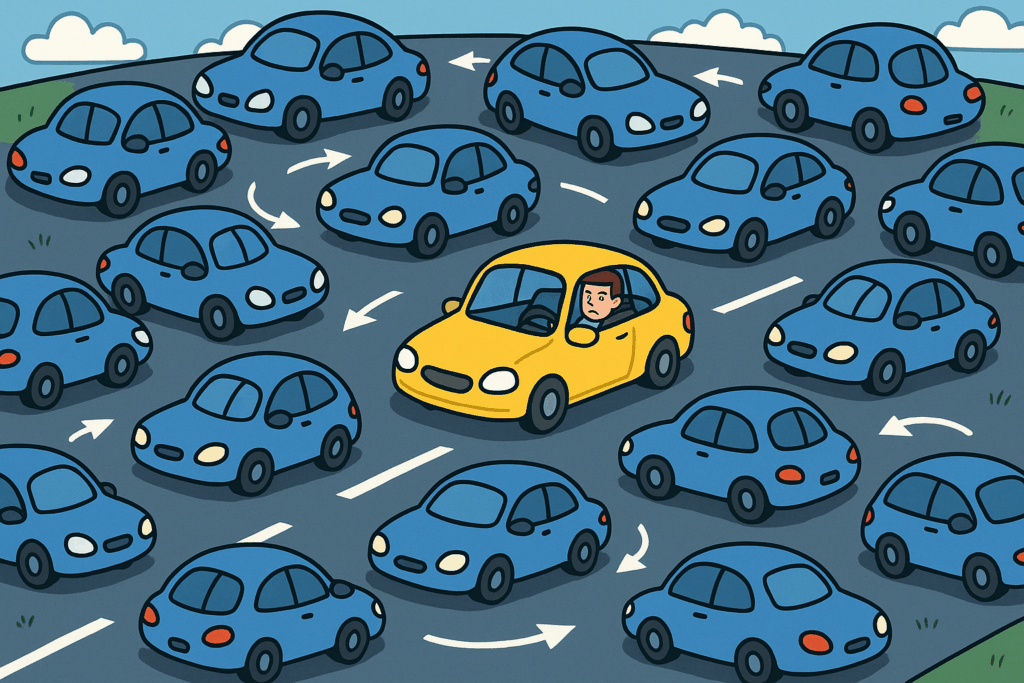
The goal isn’t to steal data but to stop normal operation. That can mean crashing a website, disabling an app, or slowing down online services so badly that users give up trying to connect.
Attackers typically use botnets, large collections of hijacked computers, routers, and even Internet of Things (IoT) devices like security cameras or smart doorbells. Once infected with malware, these devices wait for a command to send endless requests to a chosen target. Because the traffic seems to come from many different sources, blocking it is much harder than cutting off one bad actor.
If you want a quick refresher on how requests travel across the internet and how a VPN can mask the origin along that path, X-VPN’s VPN tunnel explainer breaks it down clearly.
The Main Types of DDoS Attacks
DDoS attacks come in several forms, depending on which part of the network they target. Understanding the differences helps you recognize warning signs early.

Volumetric attacks are the most common and easiest to imagine. They flood a server with more data than its bandwidth can handle. Examples include flooding connectionless protocols like UDP and ICMP to overwhelm the network’s capacity, making it unreachable.
Some attacks exploit weaknesses in network protocols, such as targeting the handshake mechanism in TCP. Instead of using raw bandwidth, they consume server resources such as connection tables or firewalls. A single machine can sometimes cripple a poorly configured system by repeatedly sending half-open connection requests.
Application-layer attacks are more sophisticated. Rather than flooding the network, they mimic normal web traffic, like sending thousands of fake “search” requests or form submissions, to overwhelm a specific app or website. Because the requests can look legitimate, these attacks are harder to filter quickly.
Each category targets a different layer of the Transmission Control Protocol/Internet Protocol (TCP/IP) stack, which underpins all internet communication. You can read more about those layers in this overview of TCP/IP.
Why DDoS Attacks Are Increasing?
DDoS attacks have grown rapidly in recent years for a few simple reasons: they’re cheap, automated, and often politically or financially motivated. Ready-made DDoS kits are sold on the dark web for less than the price of a fast-food meal, making them accessible to anyone with minimal technical skill.
Botnets have also become easier to build. Every unsecured IoT device connected to the internet can become part of an attack network. Researchers have discovered that smart light bulbs, baby monitors, and DVRs are unknowingly participating in global botnets, millions-strong.
Some attackers use DDoS as a distraction. While technical teams scramble to restore service, hackers slip in through another route to steal data or install ransomware. Others do it simply to test their capabilities or to extort companies by threatening another round unless paid off.
Even individuals aren’t immune. Online gamers are frequent targets of small-scale DDoS attacks meant to force them offline during competitions or streams.
For a broader look at threats and defenses, see X-VPN’s guide on how a VPN protects you from hackers.

How to Recognize a DDoS Attack?
Sudden slowdowns, repeated disconnects, or “service unavailable” errors might hint at a DDoS, but not every outage means an attack.
To confirm, check for unusual spikes in traffic from unfamiliar regions, alerts from your internet provider about high bandwidth use, or slow speeds simultaneously across all devices.
If your connection drops repeatedly and others nearby experience the same, contact your ISP. They can check if your network is under stress or part of a wider incident. When you suspect targeting, you can quickly verify your public endpoint with X-VPN’s IP address checker.
Personal-level DDoS Defense
For most individuals, total prevention isn’t possible, and no one can control the global internet, but you can make yourself a much harder target.
Secure your home network. Many small-scale attacks begin when attackers hijack devices to build botnets. Check your router’s firmware, disable remote management, and use a long, unique password for both Wi-Fi and admin access. If available, enable WPA3 encryption for your wireless network.
Keep software updated. Outdated systems are prime targets for malware that turns devices into DDoS bots. Turn on automatic updates for your router, operating system, and connected gadgets.
Use a reliable VPN. A VPN hides your real IP address behind a shared server address. That means attackers can’t easily locate your true connection point to launch a direct flood. VPN encryption shields your data and makes it far more difficult for a DDoS attacker to find your origin IP.
If you’re gaming or hosting a small website from home, a VPN can add an extra layer of privacy by keeping your real network details hidden from public lobbies or chat servers. Avoid exposing your IP in forums, stream overlays, or peer-to-peer apps that broadcast network information. Some services offer obfuscation to disguise VPN traffic, reducing the chance that attackers can even detect that you’re using protection.
DDoS Protection for Websites and Small Businesses
If you run a website or online shop, even brief downtime can be costly.
Here’s how to harden your setup:
- Use a content delivery network (CDN) to spread traffic loads.
- Configure rate limits and firewall rules.
- Keep offline backups of essential data.
The key is preparation, because once an attack starts, it’s too late to install protection. For businesses, pairing these tools with a VPN adds encrypted, private access for remote staff. Read more about professional VPN use in Do I really need a VPN?.
How VPNs Help Mitigate DDoS Attacks
A VPN isn’t a complete DDoS shield, but it’s a powerful defense for individuals and small teams. When you connect through a VPN, your traffic passes through an encrypted tunnel and exits from the VPN’s shared server IP rather than your own. If someone tries to retaliate or overload your connection, the VPN server absorbs the attack while your real IP remains hidden.
Some advanced VPN protocols, such as X-VPN’s Everest Protocol, use obfuscation techniques to make VPN traffic blend in with regular web traffic. That means attackers, and sometimes even restrictive networks, can’t easily detect or block your connection.
Another layer of safety comes from features like a VPN kill switch. This automatically blocks your device’s internet access if the VPN connection drops, preventing your real IP from leaking mid-session. If a server is affected, reconnecting to another location can restore service quickly without exposing your origin IP.
Don’t worry about extra fees—X-VPN offers a 100% free version for all users. Click the download button below to experience Everest and Kill Switch instantly, no login required and no traffic limits.
Protect Yourself Against DDoS Attack via X-VPN
100% free version offered.
What to Do If You’re Under Attack?
Even with precautions, no system is completely immune. If you believe you’re experiencing a DDoS attack, quick action can help limit the damage.
Disconnect and reconnect. Restart your router and, if using a VPN, switch to a different server. That changes your IP address, cutting off the attacker’s target.
Notify your internet service provider. ISPs can reroute traffic, apply temporary filters, or assign a new IP. Some providers have automatic DDoS mitigation systems for residential customers.
Limit your exposure. If the attack targets a specific app or game, log out and avoid reconnecting immediately. Attackers often move on when they lose the connection.
For websites or servers, enable emergency defenses. Activate CDN protection or firewall rate-limits if those features are available. If you use a hosting service, contact their support line for assistance.
Document what happened. Note the time, duration, and effects of the slowdown. If attacks repeat, this information helps your provider trace the source.
Most attacks are short-lived, so most home users can simply wait for a network reset. Once the attacker loses interest or your IP changes, normal service usually returns within minutes. If you want to double-check that DNS is flowing through a protected path after you reconnect, run X-VPN’s DNS leak test.

Preventing Your Devices from Becoming Part of a Botnet
The other side of the DDoS equation is making sure your own equipment never joins a botnet. Many people participate in attacks unknowingly because malware quietly runs in the background.
Every protected device reduces the power of global botnets, improving security for everyone.
If you want a quick refresher on how a VPN’s encrypted tunnel keeps device traffic out of reach on risky networks, X-VPN’s concise VPN guide covers the basics.
Here’s how to stay off the attacker’s team:
- Update your devices and change default passwords immediately after purchase.
- Disable unused remote access features.
- Install reputable antivirus software and run regular scans.
- Check your router’s connected-device list for anything unfamiliar.
- Use a VPN connection on untrusted Wi-Fi networks to keep data secure.
Why Prevention Matters
It’s tempting to think DDoS attacks only affect large corporations or government agencies, but smaller targets can suffer lasting consequences. An online store that goes down for even an hour can lose sales, while gamers or remote workers may lose data or reputation if they’re repeatedly knocked offline.
DDoS protection isn’t just about uptime, but also about control. When someone can cut off your access at will, they hold power over your ability to communicate and work. Tools like VPNs, firewalls, and careful network configuration put that control back in your hands.
Cybersecurity experts often describe DDoS mitigation as a layered defense. You can’t rely on one tool alone, but combining secure hardware, updated software, and encrypted connections creates a much more resilient system. For a practical layer that prevents IP exposure if the VPN disconnects, review this in-depth kill switch overview.
The Future of DDoS Attacks
As internet speeds increase and connected devices multiply, DDoS attacks will continue evolving and becoming more powerful. Attackers are already experimenting with artificial intelligence to coordinate smarter, more adaptive floods that shift tactics mid-attack. At the same time, new security protocols and machine-learning defenses are improving the ability to filter bad traffic automatically.
Future home routers may include built-in DDoS resistance, and VPN services are expanding to handle more mitigation at the network edge. X-VPN’s global infrastructure already routes encrypted traffic through optimized servers that can absorb spikes, helping maintain speed even under heavy load.
Still, the best defense remains awareness. Knowing how DDoS attacks work makes them far less frightening. Once you understand the signs and keep your protection tools updated, they become just another manageable risk in the digital landscape.
FAQs
What’s the difference between DoS and DDoS?
A DoS (Denial of Service) attack comes from one source, while a DDoS (Distributed Denial of Service) uses multiple devices worldwide. The “distributed” part makes DDoS attacks harder to block because there’s no single origin to shut down.
Can a VPN completely prevent DDoS attacks?
A VPN can’t stop every type of attack, but it hides your real IP address and absorbs much of the impact. Leading services employ strong encryption backed by a failsafe kill switch to help protect your online activity for personal use and remote work.
Are DDoS attacks illegal?
Yes. Launching or participating in a DDoS attack violates computer crime laws in most countries, even if done for “testing.” It’s legal to test your own systems, but attacking others without consent is punishable by fines or imprisonment.