Scientists are racing to protect our data from the most powerful computers ever imagined — before they even exist.
That sentence sounds dramatic, but it reflects a very real shift happening quietly across the internet.
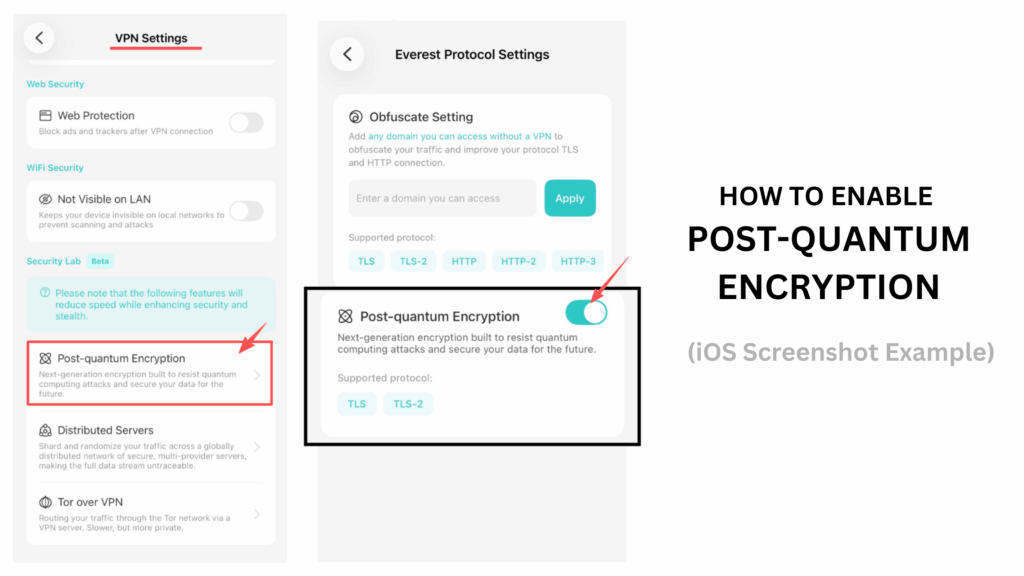
X-VPN has added support for Google’s post-quantum cryptography (PQC) approach in standard TLS and TLS-2 protocols. This isn’t a flashy new feature, and it won’t suddenly change how your VPN feels to use. Instead, it’s part of a longer timeline — preparing today’s infrastructure for risks that may only fully appear years from now.
It’s also important to be clear about what this does and doesn’t mean. Post-quantum cryptography only provides full protection when both sides of a connection support it. Right now, adoption across the internet is uneven. So this upgrade is less about immediate payoff, and more about making sure the foundations are ready before pressure arrives.
Security rarely fails all at once. More often, it breaks when systems are forced to adapt too late.
Supporting post-quantum cryptography is part of X-VPN’s long-term security planning — strengthening what works today while quietly preparing for what may come next. Nothing changes for users overnight, and that’s intentional. The goal is to make future transitions smoother, not disruptive.
Table of Contents
Why Encryption Matters in Everyday Life
Encryption isn’t something most people think about — which is exactly how it should be.
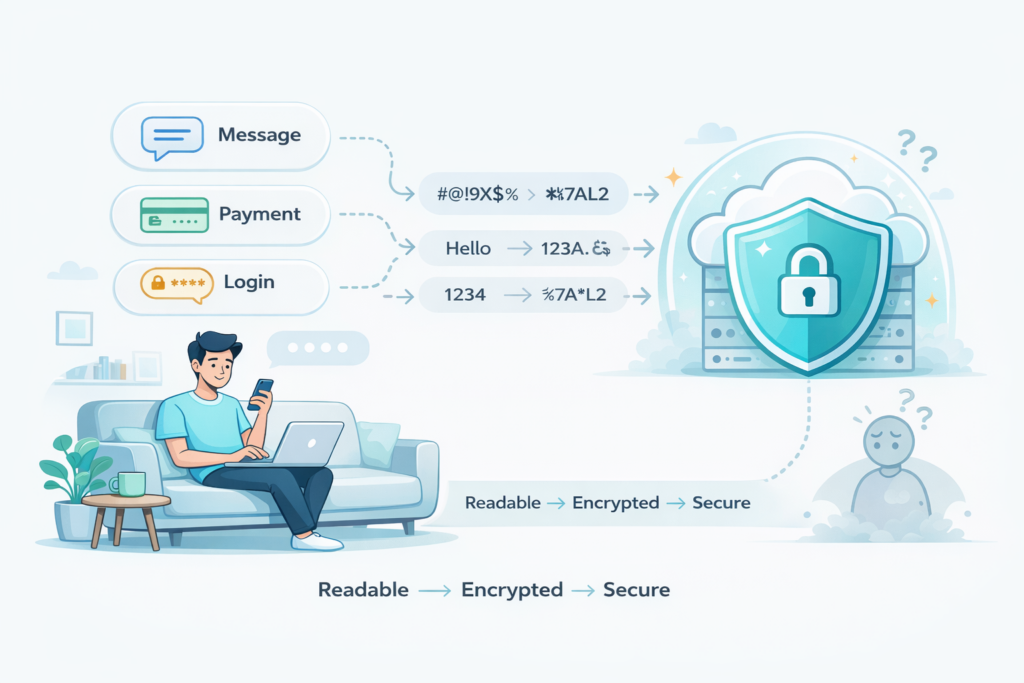
Every time you send a message, check your bank account, pay for something online, or log into an app, encryption is already doing its job. It works silently in the background, turning readable information — passwords, messages, payment details — into data that looks meaningless to anyone who shouldn’t see it.
At its core, this protection relies on a simple imbalance: some math problems are easy to do one way, but extremely hard to undo.
Multiplying two large numbers is trivial for a computer. Figuring out which two numbers created the result can take millions of years with today’s machines. That gap is what keeps your messages private and your accounts safe.
And for now, it works remarkably well.
The question isn’t whether encryption works today — it’s whether it will still work tomorrow.
The Quantum Computing Threat
Quantum computers don’t just run faster versions of the same calculations. They work differently.
Traditional computers process information using bits — either a 0 or a 1. Quantum computers use qubits, which can exist in multiple states at once. That difference allows quantum machines to explore certain problems in parallel, rather than step by step.
For most everyday tasks, that doesn’t matter. For encryption, it matters a lot.
Why This Is Important
In 1994, mathematician Peter Shor showed that a sufficiently powerful quantum computer could, in theory, break many of the encryption systems we rely on today — including RSA and ECC.
Those quantum machines do not exist yet. But many experts believe they could arrive within the next 10 to 20 years.
If that happens, encryption that would take today’s computers millions of years to break could be reduced to hours or minutes.
The impact would not be abstract. It could affect:
- financial transactions and banking systems
- government and military communications
- medical and health records
- business secrets and intellectual property
- critical infrastructure that societies depend on
This creates not just a future concern, but a present-day risk model.

“Harvest Now, Decrypt Later”
One of the most serious quantum risks is not a dramatic attack in the future — it is a quiet one happening today.
Attackers can already intercept encrypted data, store it for years, and decrypt it later once quantum computing becomes powerful enough. This strategy is known as “harvest now, decrypt later.”

The most immediate quantum risk is not future decryption, but data being captured today and decrypted years later.
This is why security teams are not waiting for quantum computers to fully arrive before acting.
Where X-VPN Fits In
X-VPN’s support for post-quantum cryptography follows this same logic.
By adding Google’s post-quantum cryptography (PQC) approach to standard TLS and TLS-2 protocols, X-VPN is aligning with how the wider internet is preparing for long-term cryptographic change. This approach focuses on compatibility — allowing new protections to be layered onto existing systems without breaking what already works.
It’s also important to be realistic. Post-quantum cryptography only becomes fully effective when both sides of a connection support it, and that’s not yet universal. Today, this work is about readiness, not guarantees.
The alternative — waiting until change becomes urgent — tends to be far more disruptive.
Keep Your X-VPN App Up to Date
X-VPN introduced support for Google’s post-quantum cryptography (PQC) approach in its standard TLS and TLS-2 protocols starting with the late December 2025 release.
To ensure compatibility with the latest security updates, make sure you’re using the most recent version of the X-VPN app. You can download or update the app from the official X-VPN VPN Download page.
The same app supports both free and premium use. You can start using X-VPN immediately as a guest with no account required, or log in to access premium features if you have a subscription.
Before going further, it helps to understand what post-quantum cryptography actually is — and what it isn’t.
What Is Post-Quantum Cryptography?
Post-quantum cryptography (PQC) is designed to protect data from both today’s computers and future quantum computers.
Here’s the key point:
Post-quantum cryptography does not require quantum computers.
Despite the name, post-quantum cryptography does not require quantum computers. These algorithms run on the same phones, laptops, and servers we use today. What changes is the mathematics underneath — it is designed to resist both classical and quantum attacks.
Rather than replacing existing encryption overnight, PQC is typically deployed alongside traditional cryptography in a hybrid approach.
In practice, this means two layers of protection work together:
- traditional encryption, which is proven against today’s threats
- post-quantum encryption, designed to resist future quantum-based attacks
Only if both layers were compromised would encrypted data be exposed.
How Post-Quantum Cryptography Is Added in Practice
Post-quantum cryptography is introduced during the encryption handshake — the brief exchange where two systems agree on keys before establishing a secure connection.
Compared to traditional handshakes, post-quantum handshakes are larger. This is not inefficiency, but a direct consequence of lattice-based cryptography operating in high-dimensional mathematical space.
Traditional vs. Post-Quantum Cryptography
Traditional systems such as RSA and ECC rely on problems like large-number factorization or elliptic curve discrete logarithms. A sufficiently powerful quantum computer could solve these efficiently using Shor’s algorithm.
Lattice-based cryptography, such as ML-KEM (formerly Kyber), takes a different path. Encryption is transformed into a problem of finding specific points inside a complex, high-dimensional lattice — a structure for which no efficient quantum shortcut is known.
Even with quantum computers, the best-known attacks remain exponentially expensive.
Hybrid Key Exchange
To remain secure during the transition period, Google introduced a hybrid key exchange design in TLS 1.3.
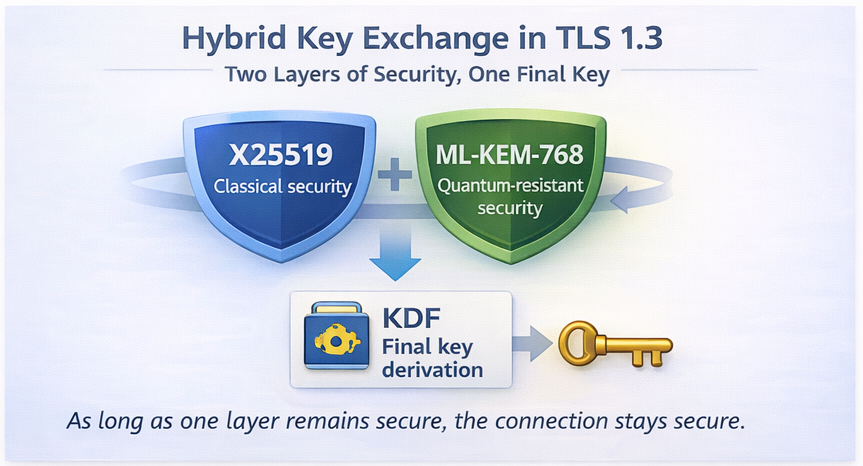
A common example is X25519MLKEM768, where:
- X25519 provides classical elliptic-curve security
- ML-KEM-768 provides post-quantum protection
Both key materials are generated during a single handshake and combined using a key derivation function.
Hybrid key exchange is designed so that as long as at least one cryptographic system remains secure, the connection remains secure.
Why the Handshake Gets Larger
In the client’s key_share extension, the total size is typically around 1,216 bytes, made up of:
- ML-KEM-768 public key (1,184 bytes)
- X25519 public key (32 bytes)
By comparison, a traditional X25519-only handshake requires just 32 bytes.
This size increase reflects the mathematical complexity needed to achieve quantum resistance, not brute-force padding.
On the server side, a similar amount of data is exchanged, including an ML-KEM ciphertext of roughly 1,088 bytes.
Because of this, the TLS ClientHello message may exceed the common MTU of 1,500 bytes, requiring packet fragmentation. Some legacy network devices struggled with this in 2024–2025, highlighting the real-world challenges of cryptographic evolution.
For users, however, this entire process remains invisible.
Why TLS and TLS-2 Matter
Not all encryption protocols can support post-quantum cryptography.
Standard TLS and TLS-2 protocols include built-in extension mechanisms. These allow new cryptographic methods—such as PQC—to be added without breaking compatibility with existing systems.
This flexibility is the main reason PQC adoption today is focused on TLS-based protocols.
Other non-standard or self-developed protocols often lack this extensibility. In those cases, supporting PQC would require major redesigns or a complete rewrite of the protocol.
As a result, even the most advanced VPN providers today can realistically support post-quantum cryptography only at the TLS/TS layer.
Client Support vs. Server Support
Post-quantum cryptography only provides full protection when both sides of a connection support it.
If a server doesn’t support PQC, the connection simply falls back to traditional encryption. Security isn’t reduced, and performance stays the same. This fallback behavior is intentional — it allows the internet to transition without breaking existing services.
You can think of it like a language transition. If both sides speak the new language, they use it. If not, they fall back to what they both understand.
Global Standards Are Already Taking Shape
Post-quantum cryptography is not being developed in isolation.
Since 2016, the U.S. National Institute of Standards and Technology (NIST) has coordinated a global effort to evaluate and standardize quantum-resistant encryption. Cryptographers, universities, and security researchers worldwide contributed to this process.

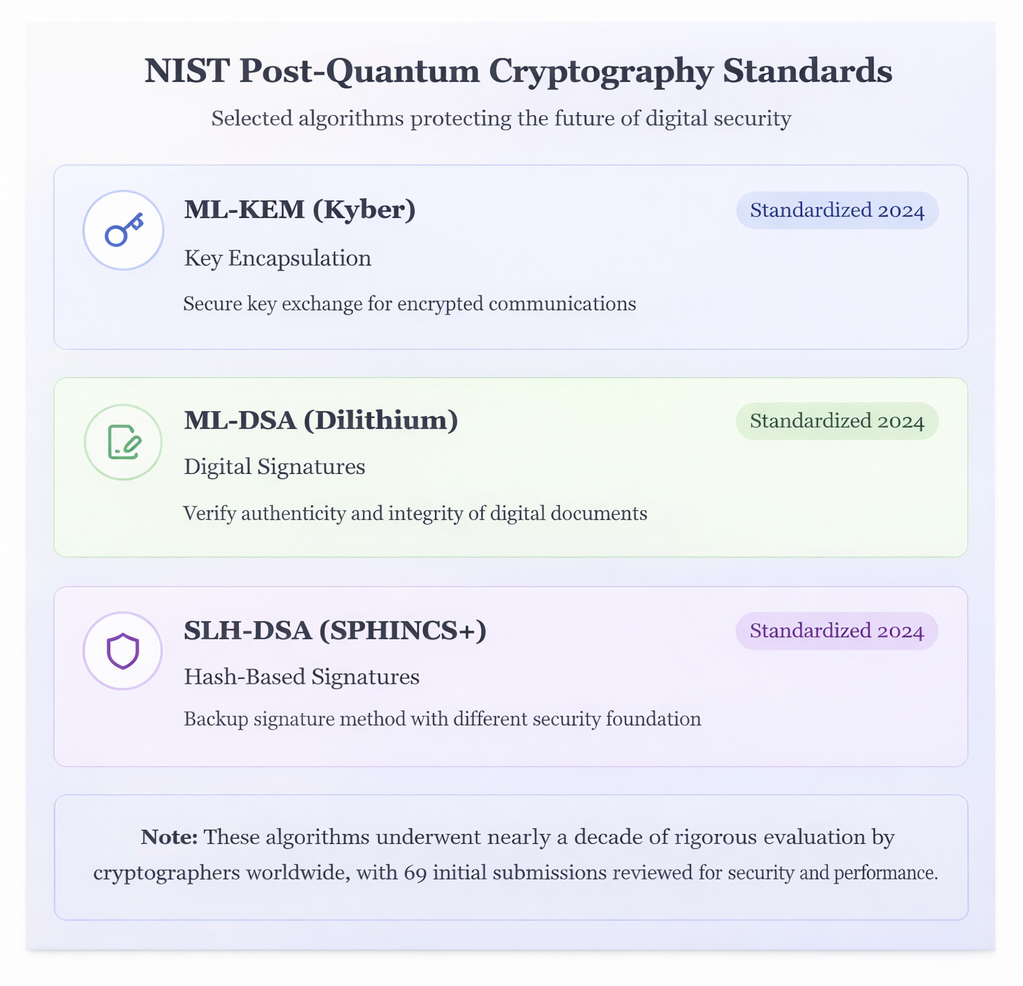
After reviewing 69 candidate algorithms, NIST finalized its first post-quantum cryptography standards in 2024. These include:
- ML-KEM (Kyber) for secure key exchange
- ML-DSA (Dilithium) for digital signatures
- SLH-DSA (SPHINCS+) as a hash-based backup option
These standards were publicly tested and analyzed for nearly a decade. The goal was not just strong theory, but real-world reliability across different devices and environments.
This matters because it signals coordination. Post-quantum cryptography is no longer experimental—it is becoming part of the internet’s long-term security foundation.
Post-Quantum Protection Is Already Being Used
This shift isn’t theoretical. It’s already happening.
- Google began testing post-quantum mechanisms in Chrome years ago and now uses them internally
- Apple introduced PQ3 for iMessage
- Signal added quantum-resistant protection in 2023
- Infrastructure providers such as Cloudflare offer post-quantum options
The transition is gradual, but it is underway.
What Post-Quantum Cryptography Does—and Doesn’t—Change Today
Post-quantum cryptography is not a switch that suddenly makes all connections quantum-proof.
What it does:
- prepares systems for future quantum-based attacks
- reduces long-term exposure to “harvest now, decrypt later” risks
- allows gradual, non-disruptive upgrades
What it does not:
- instantly protect every connection everywhere
- override servers that have not adopted PQC
- replace the need for strong classical encryption today
Understanding this distinction helps set realistic expectations and avoids unnecessary hype.
Why Acting Early Matters
Quantum computers capable of breaking today’s encryption don’t exist yet.
But security transitions take time, and data captured today may need to stay private for decades. Preparing early allows the internet to evolve calmly rather than react under pressure.
Looking Ahead
With global standards in place and real-world deployment already happening, the internet is changing — quietly, carefully, and deliberately.
X-VPN’s support for post-quantum cryptography follows that same philosophy: protect what works today, and prepare for what comes next.
Because when major shifts arrive, the safest position is to already be ready.
FAQ: Post-Quantum Cryptography
Does post-quantum cryptography require quantum computers?
No. Despite the name, post-quantum cryptography runs entirely on today’s computers, phones, and servers. The term “post-quantum” refers to the mathematical problems used, which are designed to remain difficult even if powerful quantum computers become available in the future.
Will this slow down my VPN or affect performance?
For most users, there is no noticeable impact. Post-quantum cryptography adds some additional work during the initial connection handshake, but once the secure tunnel is established, normal traffic runs as usual. The hybrid approach is designed to improve long-term security without sacrificing everyday performance.
What happens if a server doesn’t support post-quantum cryptography?
If the other side of the connection does not support PQC, the system automatically falls back to traditional encryption. Security is not reduced, and the connection continues normally. This fallback behavior is intentional and allows the internet to transition gradually rather than forcing immediate, disruptive changes.
Is post-quantum cryptography already standardized?
Yes. The U.S. National Institute of Standards and Technology (NIST) finalized its first set of post-quantum cryptography standards in 2024 after nearly a decade of public review and testing. These standards now serve as a foundation for long-term adoption across the industry.
What does X-VPN’s post-quantum support mean for me today?
Today, it means your VPN is prepared as the broader ecosystem evolves. Full post-quantum protection depends on adoption across servers and services, but X-VPN’s support ensures that you won’t need disruptive changes later. As more of the internet adopts PQC, the benefits will apply automatically.